
How Immutable Logs Ensure SOX Compliance
How Immutable Logs Ensure SOX Compliance
Immutable logs are a game-changer for meeting SOX compliance. They provide unchangeable, tamper-proof records of system events, ensuring financial data integrity and audit trail reliability. SOX Section 404 mandates companies to demonstrate effective internal controls and maintain secure, verifiable logs for up to seven years. Here's how immutable logs help:
- Tamper-Proof Records: Cryptographic hashing (e.g., SHA-256) and WORM (Write Once, Read Many) storage prevent modifications or deletions.
- Audit Trail Integrity: Logs capture user actions, changes, and access, making it easy to trace financial data events.
- Retention Compliance: Logs must remain intact, accessible, and secure for the required seven-year period.
- Cybersecurity Alignment: Protects against both internal manipulation and external breaches, critical for SOX compliance.
By using tools like AWS S3 Object Lock or Azure Blob immutability, companies can implement secure storage, role-based access control, and automated retention policies. These measures not only satisfy regulatory requirements but also streamline audits and reduce compliance costs.
Key Takeaway: Immutable logs are essential for SOX compliance, offering a secure, tamper-proof way to maintain audit trails and protect financial reporting integrity.
What Are Immutable Logs?
Definition and Key Characteristics
Immutable logs are unchangeable records that securely document digital events. Once an entry is added, it cannot be altered, deleted, or overwritten - even by system administrators. This is a key distinction from traditional logs, which can often be modified, leaving them vulnerable to tampering.
What makes immutable logs stand out is their append-only design. Unlike conventional databases that allow operations like "Update" or "Delete", these logs only permit new data to be appended to the end. This ensures that every previous entry remains intact and unaltered, effectively safeguarding the integrity of the data.
A key technology behind this is WORM (Write Once, Read Many) storage. This storage method locks data for a predefined retention period, ensuring it cannot be erased. Coupled with strict access controls, this approach creates what compliance auditors refer to as a "chain of custody" - a complete, unbroken history of all recorded events. This is particularly valuable for meeting regulatory requirements, such as those outlined in SOX audits.
Technical Process Behind Immutable Logs
The immutability of these logs is achieved through cryptographic hashing, often using algorithms like SHA-256. Each log entry is assigned a unique hash - a digital fingerprint that changes entirely if even a single character is altered. These hashes are then structured into a Merkle tree, where each new block includes the hash of the previous block. This creates a chain of dependencies: any attempt to modify an entry disrupts the entire chain, making tampering immediately obvious.
A practical example of this is the Go Checksum Database (sum.golang.org), introduced in May 2022. This system uses a transparent log built on RFC 6962 to store hashes of Go modules. By leveraging Merkle trees, the system ensures that no log entry from a previous version is ever dropped, effectively preventing attackers from introducing malicious code [4]. Similarly, Certificate Transparency projects use the same principles to maintain public, verifiable logs of issued SSL/TLS certificates. This allows domain owners to detect any improperly issued certificates.
Additional safeguards include audit paths, which verify individual log entries without requiring the entire log, and consistency proofs, which confirm that all previous records are preserved in the correct order. As Farhan Ali Khan explains:
"A tamper-evident log makes it impossible for a malicious insider to cover their tracks. A tamper-evident log discourages malicious behaviour by increasing the chance of discovery" [4].
SOX Compliance Requirements for Audit Trails
SOX Section 404 and Internal Controls
Section 404 is a key part of SOX compliance for publicly traded companies. It requires companies to create, document, and maintain a solid internal control system for financial reporting [5][8]. This isn't just about having policies in place - management must also perform an annual assessment (404a) of how effective these controls are, with the findings included in the annual report [5][6].
For larger companies with more market exposure, there's an extra step: independent auditors must verify and attest to management's assessment (404b) [5][6]. However, smaller companies with a public float under $75 million and Emerging Growth Companies earning less than $1 billion annually are exempt from this external audit requirement. They still need to complete the internal management assessments, though [5].
Audit trails play a critical role here. They must capture transaction details with enough precision to ensure accuracy [6]. These systems should track both privileged and standard user access to critical systems [8]. The goal? Forensic readiness. This means logs should clearly show who accessed, changed, or deleted records, making it possible to reconstruct events if needed [7][8]. To protect these logs, they must be stored in a way that prevents tampering, often using Write-Once-Read-Many (WORM) storage [7][8]. These controls are essential for ensuring data integrity and creating a reliable audit framework.
Retention and Integrity Requirements
SOX doesn’t just require keeping logs - it demands that they remain intact for seven years [7]. This includes audit workpapers, supporting documents, and any records tied to financial audits [7]. The SEC highlights the importance of this retention, noting that "Increased retention of identified records also may provide critical evidence of financial reporting impropriety or deficiencies in the audit process" [9].
For the first two years of this seven-year period, records must be readily accessible for SEC inspections and audits [7]. This means organisations can’t simply archive them into hard-to-reach formats. Even if legacy systems are retired, the data must stay searchable and readable for the full retention period [10]. The penalties for non-compliance are severe: corporations could face fines up to $5 million, and executives risk up to 20 years in prison for altering or destroying records [10].
How Immutable Logs Meet SOX Standards
Tamper-Proofing and Non-Repudiation
Immutable logs ensure that once an event is recorded, it cannot be secretly altered or erased. Each log entry is made permanent, even system administrators cannot modify or delete it. This is achieved using cryptographic safeguards, particularly SHA-256 hashing, which generates a unique digital fingerprint for every log entry. If someone tries to tamper with a record, the fingerprint changes, making the interference immediately obvious. This level of integrity satisfies SOX's requirement for reliable audit trails, especially during Section 404 assessments, giving auditors confidence that the data they review is authentic and untampered.
On top of this, WORM (Write Once, Read Many) systems provide an additional layer of assurance, ensuring records remain unchanged for their entire lifecycle.
WORM (Write Once, Read Many) Systems
WORM systems are a cornerstone of SOX-compliant immutable logging. They guarantee that once a log is written, it cannot be modified, overwritten, or deleted during its retention period. This is particularly crucial for meeting the demands of SOX Section 404. Ashok Kumar N, Senior Architect at Archon Data Store, explains:
"WORM is not just a feature - it is a verifiable process ensuring financial records are preserved and retrievable throughout their lifecycle" [11].
Cloud providers like AWS and Azure offer WORM functionality through tools such as AWS S3 Object Lock and Azure Blob Storage immutability policies. For SOX compliance, organisations must use Compliance Mode, as it prevents even root users from deleting records [13]. Microsoft advises locking these policies within 24 hours of creation to align with SEC 17a-4(f) rules [12]. While some systems support retention periods as long as 146,000 days (nearly 400 years), financial reporting generally requires data to be retained for six years [11][12].
Long-Term Retention and Access Control
SOX compliance isn't just about storing records - it’s also about ensuring they remain secure and accessible for the required retention period, which is often seven years.
This is where robust access controls and monitoring come into play. Role-based access control (RBAC) limits who can view logs, while secondary audit trails keep track of every access attempt, holding users accountable. Data is often stored in tiers: an active database with real-time monitoring for six months, an intermediate archive with hash verification, and a final archive secured with WORM storage and AES-256 encryption [1]. Accurate timestamps are also critical for audits, which is why synchronised time sources via secure NTP are used to ensure precise event tracking [1]. Even when legacy systems are retired, the data must remain accessible and readable in electronic formats throughout the retention period [11].
Implementing Immutable Logs for SOX Audits
Selecting a Log Management Platform
Picking the right log management platform is a key step toward SOX compliance. To maintain a tamper-proof chain of custody, look for platforms that utilise WORM (Write Once, Read Many) storage and cryptographic hashing methods like SHA-256 or blockchain-based techniques. These features help ensure that any tampering is immediately detectable.
It's equally important to enforce Role-Based Access Control (RBAC). This means assigning specific roles to users, such as:
- Log Viewers: Limited to read-only access.
- Log Analysts: Allowed to perform searches within logs.
- Log Administrators: Granted full management capabilities.
For organisations in France or other European countries, data sovereignty is a critical factor. Platforms like LogCentral, hosted within Europe, not only comply with GDPR but also provide SOX-compliant audit trails. They even support multi-tenancy, which is particularly useful for managed service providers (MSPs) handling multiple clients.
Secure data transport is another must-have feature. Ensure the platform supports TLS 1.3 on port 6514 with certificate validation to secure log ingestion. Additionally, the platform should automate the log lifecycle, including archiving and secure deletion, while offering retention capabilities of at least seven years to satisfy regulatory requirements.
Once you've selected a platform, configure it to enforce SOX-specific retention and security measures.
Configuring Retention Policies and Security
After choosing the platform, the next step is to set up retention policies that preserve the audit trail securely. Start by enabling Network Time Protocol (NTP) across all systems. This ensures synchronised timestamps, which are critical for maintaining a legally defensible and chronological audit trail [14].
SOX regulations require automated retention policies. These should move logs through three stages:
- Real-time monitoring
- Intermediate archiving with hash verification
- Immutable long-term storage
To reduce the risk of tampering, use separate storage pools for operational logs (actively monitored) and archived logs (restricted access).
Accountability is another key factor. Log every instance of administrator access to the log management platform [1]. This not only ensures compliance but also helps identify any unauthorised internal activity. Finally, enhance your security setup with automated threat hunting using parameterised queries and Sigma rules [2]. This proactive approach strengthens the system's defence against potential threats.
What Does It Mean for Digital Evidence or Logs to Be Immutable?
Comparing Immutable Log Solutions
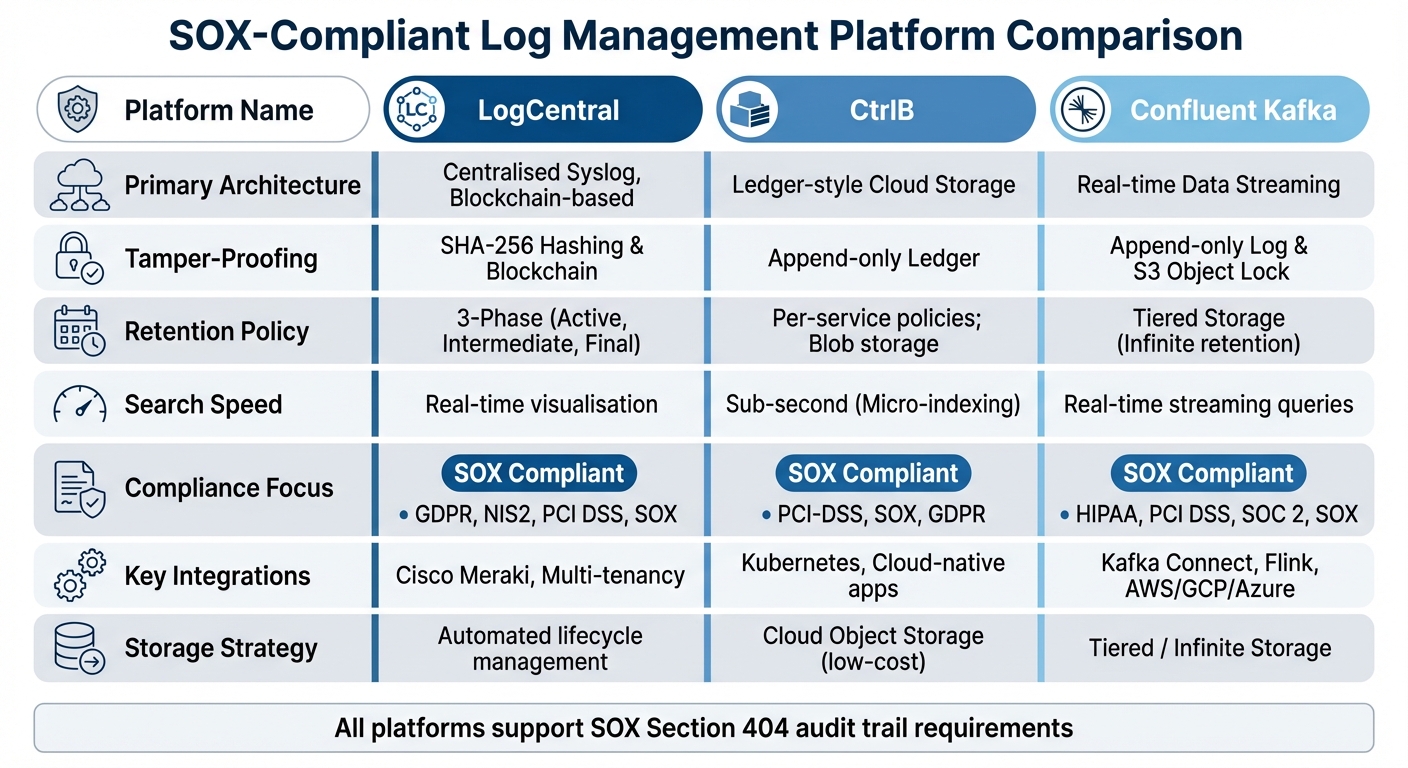
Comparing SOX-Compliant Immutable Log Management Platforms
Log Management Platform Comparison
When it comes to safeguarding SOX audit trails, choosing the right platform is critical. Each solution offers unique strengths in areas like immutability, performance, and compliance. Here's a breakdown of three leading platforms:
LogCentral employs a centralised syslog setup combined with blockchain verification to ensure logs remain tamper-proof. Based in Europe, it meets both SOX and European data sovereignty requirements. Its standout features include native multi-tenancy and integration with Cisco Meraki, making it particularly appealing for MSPs managing multiple clients. The platform's three-phase retention system - covering active monitoring, intermediate archiving, and immutable final storage - streamlines the log lifecycle, reducing administrative tasks while ensuring compliance.
CtrlB, on the other hand, adopts a ledger-style, append-only approach. Through micro-indexing, it delivers sub-second search speeds across years of archived data stored on cost-efficient cloud infrastructure [15]. This rapid search capability is invaluable for organisations needing to reconstruct event sequences during audits. Additionally, CtrlB's verified queries guarantee the integrity of the original logs, which is essential for maintaining a reliable audit trail.
Confluent Kafka focuses on real-time data streaming and integrates with WORM-compliant object storage solutions like Amazon S3 with Object Lock for long-term, immutable retention [3]. According to Confluent:
"The core value of an audit log is its integrity; it must be a tamper-proof source of truth" [3].
Its tiered storage model allows organisations to retain logs indefinitely while optimising costs. Furthermore, its horizontal scaling can handle high-throughput ingestion from thousands of sources simultaneously.
| Feature | LogCentral | CtrlB | Confluent Kafka |
|---|---|---|---|
| Primary Architecture | Centralised Syslog, Blockchain-based | Ledger-style Cloud Storage | Real-time Data Streaming |
| Tamper-Proofing | SHA-256 Hashing & Blockchain | Append-only Ledger | Append-only Log & S3 Object Lock |
| Retention Policy | 3-Phase (Active, Intermediate, Final) | Per-service policies; Blob storage | Tiered Storage (Infinite retention) |
| Search Speed | Real-time visualisation | Sub-second (Micro-indexing) | Real-time streaming queries |
| Compliance Focus | GDPR, NIS2, PCI DSS, SOX | PCI-DSS, SOX, GDPR | HIPAA, PCI DSS, SOC 2, SOX |
| Key Integrations | Cisco Meraki, Multi-tenancy | Kubernetes, Cloud-native apps | Kafka Connect, Flink, AWS/GCP/Azure |
| Storage Strategy | Automated lifecycle management | Cloud Object Storage (low-cost) | Tiered / Infinite Storage |
This comparison highlights how each platform caters to SOX audit trail requirements in distinct ways.
A critical feature of any solution is the enforcement of retention policies that are both immutable and resistant to administrative tampering. Additionally, systems should maintain detailed audit trails that log every access attempt or modification request relating to the audit logs - essentially creating an "audit trail for the audit trail" [1][11]. It's also vital to confirm that platforms disallow independent metadata edits, as such changes can undermine compliance with regulatory standards [11].
Conclusion
Immutable logs are at the heart of SOX compliance. As Hoop.dev aptly puts it:
"Audit logs for SOX compliance are not a checkbox. They are the factual backbone of financial data integrity" [16].
These logs ensure that once events are recorded, they cannot be altered or erased, offering the permanence and non-repudiation required under SOX Section 404. This is critical for maintaining robust internal controls over financial reporting and for ensuring compliance during audits.
SOX mandates a seven-year, tamper-proof retention policy, which is achieved through automated retention and archiving systems. Such mechanisms ensure that audit trails remain reliable and secure throughout their entire lifecycle.
To address these requirements, solutions like LogCentral simplify the compliance process. LogCentral employs a three-phase retention system - covering active monitoring, intermediate archiving, and immutable final storage - that aligns with SOX's seven-year retention standard. Fully hosted in Europe and GDPR-compliant, the platform includes features like native multi-tenancy and role-based access control, making it especially useful for MSPs and IT teams managing multiple clients. Its integration with Cisco Meraki and built-in alerting capabilities further enhance compliance workflows. Additionally, adopting immutable log solutions can cut data breach costs by over €1.55 million.
As LogCentral highlights:
"Compliance is all about controlling your systems. The way to ensure that control is through preventive and detective controls. Log management is a key component for detective controls and the workflow around them."
FAQs
How do immutable logs help ensure compliance with SOX regulations?
Immutable logs are a cornerstone for meeting SOX compliance, as they provide a tamper-proof record of all system activities. Once logged, data cannot be altered or erased, ensuring that audit trails remain intact and trustworthy. This is crucial for verifying internal controls and maintaining financial accuracy, both of which are central to SOX regulations.
These logs capture detailed information like user actions, system changes, and timestamps, enabling organisations to meet stringent regulatory requirements. By doing so, they help reduce the risk of fraud and prevent unauthorised changes, shielding businesses from potential penalties. Technologies such as cryptographic security add an extra layer of protection, ensuring long-term security and auditability of these records.
Tools like LogCentral make it easier for businesses in France to stay compliant by offering features like long-term log retention, intelligent alerts, and real-time monitoring. These capabilities streamline the process for IT teams, ensuring secure and verifiable audit trails are always maintained.
How do immutable logs help meet SOX compliance requirements?
Immutable logs use cutting-edge methods to keep log data secure, unchangeable, and traceable - key elements for meeting SOX compliance standards. One of these methods is cryptographic hashing (such as SHA-256), which creates unique digital fingerprints for each log entry. These entries are then linked in a chain, so if someone tries to tamper with a log, the broken chain makes it immediately obvious.
Another essential tool is Write Once, Read Many (WORM) storage, which guarantees that once data is recorded, it cannot be altered or deleted. This ensures the integrity of the logs over time. On top of that, encryption protects logs during their transfer and storage, shielding them from unauthorised access. Some systems even incorporate blockchain technology, enabling distributed ledgers that are resistant to tampering.
Platforms like LogCentral combine these technologies to create a secure and compliant system for managing audit trails. This helps businesses not only adhere to SOX but also comply with GDPR and other regulations focused on data integrity and accountability.
Why is immutable storage essential for SOX compliance?
Immutable storage, often called WORM (Write Once, Read Many) storage, plays a key role in meeting SOX compliance requirements. Its primary function is to ensure that data remains unchangeable and undeletable for the entire legally mandated retention period. This safeguards the integrity and reliability of records, which are essential for establishing tamper-proof audit trails.
By preserving unaltered logs, organisations can showcase accountability and meet the rigorous standards set by SOX regulations. Tools like LogCentral make this process easier by offering secure, long-term log retention along with advanced monitoring features, ensuring your data stays both accessible and protected.