
Long-Term Log Retention for SOX Compliance
Long-Term Log Retention for SOX Compliance
SOX compliance requires public companies to securely store financial logs for at least seven years. This includes audit logs, financial records, and system access logs. Non-compliance risks fines up to $5 million or 20 years in prison.
Key steps to meet these requirements:
- Retention Policy: Define what to store, how long, and who manages access.
- Log Classification: Prioritize financial, security, and IAM logs while archiving less critical data.
- Storage Tiers: Use hot (recent), warm (mid-term), and cold (long-term) storage to balance cost and accessibility.
- Automation: Implement tamper-proof systems like WORM storage and automated purging.
- Access Control: Enforce RBAC with audit trails and multi-factor authentication.
- Centralized Platforms: Simplify log management with tools like LogCentral or AWS S3.
- Testing: Regularly verify retrieval speeds, data integrity, and access controls.
- SIEM Integration: Connect logs to monitoring tools for real-time compliance and threat detection.
Choose the right tools to automate retention, prevent tampering, and maintain audit trails. For European businesses, ensure GDPR compliance with EU-hosted platforms like LogCentral.
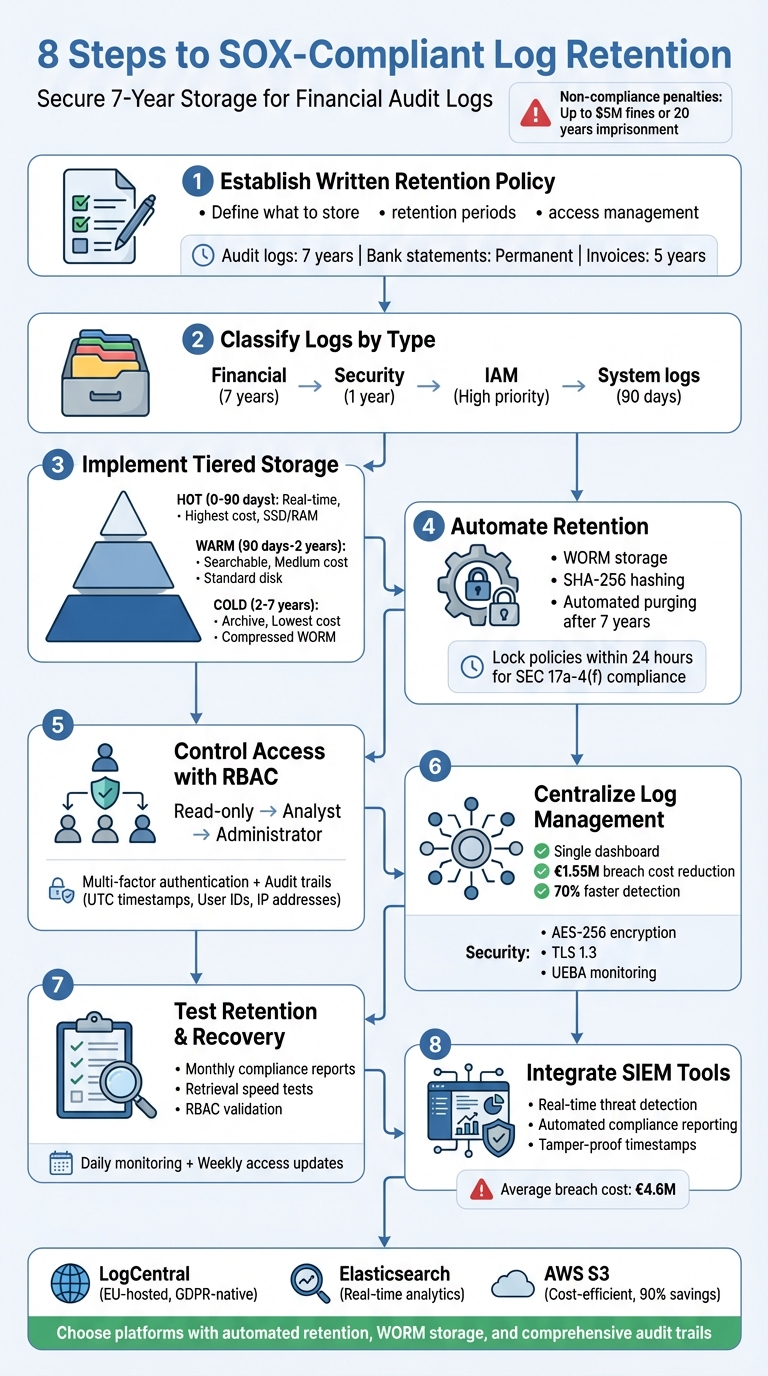
8-Step SOX Compliance Log Retention Process
2023 SOX Compliance Reporting: How to Prepare
1. Establish a Written Retention Policy
A well-documented retention policy is essential for meeting SOX compliance requirements. This policy should outline which records need to be kept, for how long, who can access them, and when or how they should be deleted.
Start by identifying all data relevant to SOX compliance. This includes general ledgers, journal entries, audit logs, financial statements, payroll records, and even supporting emails. Essentially, any record that could affect financial reporting falls under SOX regulations [3][4]. Create a centralized inventory that maps each data source to its specific retention requirements.
Here’s a quick breakdown of retention timelines:
- Audit and accounting records: Keep for seven years [4].
- Bank statements, payroll registers, and contracts: Retain permanently.
- Customer invoices and purchase orders: Store for five years [4].
Failing to comply with these rules could result in severe penalties, including fines of up to $5 million per violation or up to 20 years in prison for tampering with records [3][4].
Your policy should also include legal hold procedures. These procedures ensure that records are preserved immediately if there’s a legal investigation or audit underway [3][4]. Assign specific roles, like a CFO or IT Compliance Manager, to oversee the implementation of the retention policy and conduct annual reviews to keep everything on track [4].
To stay audit-ready, maintain clear documentation, such as data inventories, extraction logs, chain-of-custody records, and storage diagrams [3]. It’s also crucial to periodically test archived data to ensure it remains accessible and readable in formats like PDF, CSV, or XML, even if the original systems are no longer in use [3].
Once these steps are in place, focus on classifying your logs by type and priority to streamline compliance efforts.
2. Classify Logs by Type and Importance
When it comes to SOX compliance, not all logs carry the same weight. Financial application logs take the lead in importance since they directly track transactions, data changes, and system access tied to financial reporting. These logs - whether from ERP systems, accounting software, or other financial tools - must be actively monitored and retained for seven years.
Security and network logs are next in line. These logs are vital for spotting unauthorised access attempts and potential data breaches that could compromise financial data. Typically, they should be kept for one year, though this can vary based on risk levels. As The Graylog Team highlights:
"Cybersecurity and internal controls impact financial reporting accuracy in two different ways: Compromised technologies can undermine reporting accuracy and reliability, and data breaches arising from weak internal controls reduce revenue" [5].
IAM logs (Identity and Access Management) are also high-priority. These logs should capture every login, privilege escalation, multi-factor authentication update, and PAM (Privileged Access Management) activity. Since administrative accounts pose a significant risk to financial data, these logs provide critical oversight.
On the lower end of the priority scale are system configuration and operational logs. Logs documenting configuration changes, OS updates, or API interactions generally need retention for six months to one year. Meanwhile, routine system events like CPU usage spikes or service restarts can often be kept for around 90 days [5].
Once you've classified the logs, you can implement a tiered storage strategy to manage compliance costs efficiently. This classification process sets the stage for adopting storage solutions that align with both compliance and budgetary goals.
3. Use Tiered Storage for Cost Efficiency
A tiered storage strategy is a smart way to manage logs, balancing cost and accessibility. By organising logs into different storage tiers, you can keep active logs on faster, more expensive storage while archiving older logs more affordably. Here's how each tier works in a cost-efficient compliance plan:
Hot storage is designed for real-time monitoring and quick troubleshooting. This tier uses high-speed options like SSDs or RAM, making it perfect for logs from the past 0 to 90 days. While it's the priciest option, it's critical for active security alerts and operational awareness. For compliance, live logs should remain accessible for at least four days before being archived [6].
Warm storage is suitable for logs aged between 90 days and 2 years. This tier relies on standard disk or object storage and often uses searchable snapshots for efficient historical queries at a lower cost. As Logz.io explains:
"By effectively managing your data lifecycle with archiving and restoring, you can maintain performance and cost-efficiency while ensuring long-term accessibility of critical information" [6].
Cold or archive storage is the most economical option, intended for logs that need to be kept for long-term compliance, such as the seven-year SOX requirement. Logs in this tier are stored in compressed, non-indexed WORM (Write Once, Read Many) formats to prevent tampering. Retrieval is slower, but these logs are primarily used for audits or legal discovery. When necessary, you can temporarily restore logs to a searchable account for further analysis [6].
| Storage Tier | Typical Age | Retrieval Speed | Cost Profile | Primary Use Case |
|---|---|---|---|---|
| Hot | 0–90 Days | Immediate / Real-time | Highest | Real-time troubleshooting & security monitoring |
| Warm | 90 Days – 2 Years | Moderate / Searchable | Medium | Compliance reviews & incident investigation |
| Cold | 2–7 Years | Slowest / Requires restore | Lowest | Long-term SOX compliance & legal discovery |
4. Automate Retention and Prevent Tampering
Handling logs manually can jeopardize SOX compliance. By automating log retention, you ensure the required seven-year storage period is met without relying on human intervention. Automation also incorporates tamper-proof measures to safeguard log integrity. Once these systems are in place, enforce them with robust technical controls.
WORM storage (Write Once, Read Many) is a key tool for preventing edits. With time-based retention policies, logs can be created and read, but any edits or deletions are blocked for a predetermined period. To comply with regulations like SEC 17a-4(f), these policies must be locked. As Microsoft Learn states:
"A time-based retention policy must be locked for the blob to be in a compliant immutable (write and delete protected) state for SEC 17a-4(f) and other regulatory compliance" [7].
Once locked, these policies allow for extending the retention period but prohibit shortening it or deleting the policy itself [7]. Microsoft advises locking these policies within 24 hours of creation to maintain compliance [7].
Cryptographic hashing ensures log integrity by creating a unique digital fingerprint for each file using SHA-256. Even a minor alteration in the log file changes the hash, making tampering immediately detectable. This feature is particularly useful during audits, where proving that logs remain unaltered is critical.
Automated purging helps manage storage efficiently by deleting logs after the seven-year retention period. This reduces both costs and legal risks associated with keeping outdated records.
| Security Feature | Purpose | Implementation Priority |
|---|---|---|
| WORM Configuration | Prevents edits to ensure log data integrity | Critical |
| SHA-256 Hashing | Detects unauthorized changes to log entries | High |
| Automated Purging | Deletes logs after the legally required period | High |
| Digital Signatures | Confirms the origin and authenticity of logs | Medium |
5. Control Access with RBAC and Audit Trails
Controlling who can view, modify, or delete logs is a cornerstone of SOX compliance. With Role-Based Access Control (RBAC), you can assign permissions based on specific roles, ensuring that critical tasks - like creating logs versus deleting them - are handled by separate individuals. This helps maintain the integrity of audit trails, even if an account is compromised.
RBAC also streamlines permission management. Instead of assigning access to individual users, permissions are tied to roles. When employees change positions or leave the organisation, you can simply reassign or revoke their roles, reducing the risk of orphaned accounts with lingering privileges. For SOX compliance, it's a good idea to establish at least three levels of access: Read-only for basic monitoring, Analyst for search and reporting, and Administrator for system control. To bolster security, require multi-factor authentication (MFA) for roles with administrative or export permissions.
Audit trails work hand-in-hand with RBAC by recording every interaction with log data. These trails should include essential details like UTC timestamps, user IDs, action types, and IP addresses. This creates a transparent record for auditors, ensuring accountability and helping to identify any suspicious activity. As Microsoft aptly puts it:
"Security log retention is not just a compliance checkbox - it's a strategic investment in operational resilience" [8].
For example, LogCentral integrates RBAC into its multi-tenant architecture, enabling IT teams and MSPs to set precise access levels. By combining these role-based permissions with immutable audit logs, organisations can confidently show auditors that their log data remains secure and unaltered throughout the mandatory seven-year retention period. Regularly reviewing access roles and promptly revoking permissions for offboarded employees further ensures compliance.
This combination of controlled access and thorough audit trails lays the foundation for effective, centralised log management, keeping all systems in line with SOX requirements.
6. Use a Centralised Log Management Platform
Handling logs from various sources can quickly become a tangled mess, making it harder to maintain a clear audit trail. A centralised log management platform solves this by pulling all your logs into one easy-to-access dashboard. This setup ensures full visibility and simplifies SOX compliance, especially for Sections 302 and 404, which focus on accurate financial reporting. Instead of wasting time digging through multiple systems during an audit, you’ll have a single, reliable source of truth.
These platforms don’t just streamline processes - they also save money and time. For example, they can reduce breach-related costs by over €1.55 million and improve breach detection speeds by up to 70%. Plus, they handle tiered storage automatically, ensuring you meet SOX retention requirements without manual oversight. This keeps costs steady and predictable.
Security is another major benefit. Centralised platforms use advanced measures like WORM storage, SHA-256 hashing, AES-256 encryption for stored data, and TLS 1.3 for data in transit. On top of that, UEBA (User and Entity Behavior Analytics) can flag unauthorised access to financial systems in real time, addressing the SEC’s focus on cybersecurity risks tied to financial reporting [5].
Take LogCentral as an example. It offers features like native RBAC (Role-Based Access Control), long-term retention, and live log visualisation, making it an excellent choice for IT teams and MSPs managing SOX compliance for multiple clients. With European hosting, it aligns with both GDPR and SOX requirements. Look for platforms offering automated lifecycle policies, immutable storage, and fast search capabilities - these can make audit preparation much more manageable.
7. Test Retention and Recovery Procedures
Storing logs isn’t enough - you need to ensure they’re accessible and retrievable when auditors request them. Regular testing is key to confirming your retention systems function as intended and that logs can be produced within required timeframes. This involves simulating audit scenarios to verify both data accessibility and integrity across all storage tiers.
A good starting point is generating monthly compliance reports. As LogRhythm advises:
"The SOX COSO report package must be run no less frequently than once per month to ensure all data is available for report generation" [9].
These monthly checks ensure logs remain complete and accessible. In addition to automated reporting, periodically review reports like "Usage Auditing Event Detail" to confirm that investigations and administrative actions are being carried out as required [9]. This consistent testing reinforces the retention measures you’ve implemented.
Testing shouldn’t stop at automated processes. Expand your checks to include all storage tiers, especially cold storage, to confirm retrieval speeds meet compliance requirements. Run search queries on archived data and document how long retrieval takes - this ensures you’re prepared for any auditor’s timeline.
Access control testing is another critical step. Revalidate your RBAC (Role-Based Access Control) and multi-factor authentication settings to ensure auditors have appropriate access while blocking unauthorised users. Address any issues uncovered during these tests to avoid surprises during an actual audit.
Daily monitoring and incident response logging are also essential [5]. These logs provide a clear audit trail, demonstrating continuous oversight in line with SOX-COSO principles. Additionally, update privileged access records, vendor lists, and terminated employee details on a weekly basis [10]. This reduces false positives and highlights your diligence to SOX examiners. The data from these tests can also guide improvements to your centralised log management system.
8. Connect with SIEM and Monitoring Tools
Integrating log retention with a SIEM platform transforms static archives into dynamic tools for compliance and security. This step enables real-time threat detection and automated compliance reporting, both of which are essential for meeting SOX requirements. Beyond compliance, this integration helps protect financial data, with breaches averaging a cost of €4.6 million [2]. It also sets the stage for advanced analytics and smoother audits.
For SIEM platforms to work effectively, your system must meet specific technical standards. Modern SIEM tools can automatically identify anomalies - such as unauthorised logins or unusual database queries - and update incident records to create a verifiable audit trail. When a potential threat is flagged, the system immediately logs the event, ensuring SOX auditors have access to a centralised and reliable record. This single dashboard simplifies the task of monitoring compliance measures across even the most complex organisations [11].
The advantages go beyond just detecting threats. By integrating with a SIEM, compliance reports required by SOX regulators, investors, and partners can be generated automatically, significantly reducing the workload for security teams [11]. Moreover, SIEM dashboards can provide read-only access to external auditors, allowing them to verify reports without risking any unauthorised changes. David Harrison, Chief Audit Executive at Origin Bank, highlights this benefit:
"The external auditors for our organisation have found the audit log very helpful. They can find dates when a control has been modified and the effective date for that control and have all the parties work off the same process narrative" [2].
To comply with SOX Section 802, ensure your log retention system supports TLS 1.3 (via Port 6514) and uses immutable WORM storage to maintain tamper-proof timestamps and event data [11] [1]. Platforms like LogCentral, which feature RBAC, long-term retention, and live log visualisation, are excellent for feeding SIEM tools with consistent, secure data streams while staying GDPR-compliant for European organisations.
Don’t just collect logs - connect them to SOX risk factors. For instance, use authentication logs to detect credential theft, database logs to flag unauthorised queries, and integrate real-time threat intelligence feeds to minimise false positives [2]. This proactive strategy, combined with automated evidence gathering, helps ensure your organisation is always ready for an audit.
Comparison Table
To navigate the options for long-term log retention, it's important to weigh the features of leading SIEM-integrated platforms. The right platform will depend on your technical requirements, budget, and compliance needs, particularly for regulations like SOX and GDPR.
For European businesses, LogCentral, Elasticsearch, and AWS S3 each offer distinct benefits tailored to different priorities.
- LogCentral is tailored for European operations, featuring native EU-based storage and automated log purging to streamline GDPR compliance. Its subscription model includes a built-in 7-year retention policy and audit trails, eliminating the need for manual configurations.
- Elasticsearch stands out for real-time search and advanced analytics. However, long-term retention can become expensive unless Index Lifecycle Management (ILM) is carefully implemented to move data into cold storage tiers. GDPR compliance also requires manual configurations, as it depends on regional settings.
- AWS S3 excels in cost control with its tiered storage, which can cut costs by up to 90% when data transitions to cold storage after 90 days. However, SOX compliance requires manually enabling "Object Lock" in "Compliance Mode", while GDPR compliance depends on selecting EU regions (like Frankfurt or Ireland) and setting up data residency policies.
The table below highlights the key differences in retention capabilities, compliance, pricing models, and overall suitability:
| Feature | LogCentral | Elasticsearch | AWS S3 |
|---|---|---|---|
| Retention Capabilities | Automated 7-year policies | Manual via Index Lifecycle Management (ILM) | Automated via S3 Lifecycle Rules |
| SOX Compliance | Built-in 7-year retention and audit trails | Requires custom ILM and RBAC setup | Requires "Object Lock" for WORM compliance |
| Pricing Model | Subscription / Flat-fee focused | Consumption-based (Storage/Compute) | Pay-as-you-go (Tiered storage) |
| GDPR Compliance | Native EU-based storage and automated purging | Region-dependent; requires manual config | Region-dependent (e.g., Frankfurt/Ireland) |
| Best For | European MSPs and IT professionals | Real-time search and complex analysis | Low-cost archival and massive scale |
Key Takeaways
- LogCentral is the go-to choice for European businesses prioritising GDPR compliance and simplicity, as it avoids the legal hurdles of cross-border data transfers.
- Elasticsearch is well-suited for organisations needing advanced analytics, provided they have the expertise to manage ILM policies and region-specific GDPR setups.
- AWS S3 is perfect for companies handling large-scale data archives at minimal cost, though it requires manual setups for both SOX and GDPR compliance.
Conclusion
Ensuring SOX compliance for long-term log retention means securely storing audit logs for at least seven years. This requires tamper-proof methods like WORM storage or digital signatures, along with maintaining detailed audit trails that document every instance of access. These aren't just best practices - they're legal requirements, and failing to comply can lead to severe penalties.
To stay compliant, start with a clear, written retention policy. Specify which logs need to be retained, the duration, and assign responsibility for monitoring compliance. Use tiered storage: keep recent logs easily accessible while archiving older ones. Enforce RBAC (Role-Based Access Control) with proper audit trails, and regularly test your recovery processes to ensure everything works when needed.
For businesses operating in Europe, additional considerations come into play. For example, GDPR mandates that logs containing personal data must remain within EU jurisdictions. This makes EU-hosted platforms indispensable. Tools like LogCentral address such challenges, offering EU-based storage, automated seven-year retention policies, and integrated audit trails to simplify compliance.
The financial risks of poor log management are substantial. Data breaches cost an average of €4.5 million, and one-third of these breaches stem from improperly logged "shadow data" [2]. Effective log management not only ensures compliance but also protects your organisation from these costly risks.
Ultimately, choosing the right log management platform is critical. Whether it’s a specialised solution like LogCentral, a versatile tool like Elasticsearch, or a budget-friendly option like AWS S3, the priority is automating retention, preventing tampering, and maintaining comprehensive audit trails. Relying on manual processes simply won’t meet today’s regulatory standards.
FAQs
What are the consequences of not meeting SOX log retention requirements?
Failing to comply with SOX log retention rules can come with some heavy consequences, like financial penalties, legal troubles, and a hit to your organisation's reputation. SOX regulations require businesses to securely keep audit and financial records for at least seven years to maintain transparency and accountability.
If these standards aren't met, companies might face more intense regulatory oversight, potential lawsuits, and a loss of trust from stakeholders. Using a solid log management system, like LogCentral, can help ensure your organisation meets retention requirements, stays compliant, and avoids unnecessary risks.
How can tiered storage reduce costs for long-term log retention?
Tiered storage is a smart way to manage costs by automatically moving older or less-accessed logs to more affordable storage options, like warm or cold storage. This approach keeps critical logs readily available while trimming down storage expenses over time.
For organisations in France working to meet SOX compliance, tiered storage offers a budget-friendly solution that supports long-term retention needs. Tools like LogCentral make this process straightforward by providing intelligent storage management, ensuring compliance without overspending.
Why is automation important for maintaining SOX compliance in log management?
Automation plays a crucial role in upholding SOX compliance by consistently enforcing log retention policies, safeguarding data, and identifying anomalies - all with minimal manual effort. Automated systems take charge of tasks like scheduled archiving, integrity checks, and secure storage. This not only reduces the likelihood of human error but also ensures compliance with retention regulations.
Tools such as LogCentral make compliance even more manageable. They provide secure, tamper-proof storage, real-time monitoring, and automated alerts for any suspicious activities. These features not only protect the integrity of financial data but also simplify audit preparation through automated reporting and documentation. By streamlining these processes, automation helps businesses in France and beyond maintain efficiency, reliability, and strict adherence to SOX standards.