
Syslog Priority Grid: Severity vs Facility
Syslog Priority Grid: Severity vs Facility
The syslog priority grid combines severity levels (0–7) and facility codes (0–23) into a single priority value using the formula: Priority = (Facility × 8) + Severity. This creates 192 unique combinations to classify and manage log messages effectively.
For IT teams in France, understanding this system is critical for tasks like filtering, routing, and alerting logs, especially to meet GDPR compliance. Logs from sensitive facilities, such as authpriv, can be categorized to enforce strict retention and access policies. Severity levels help prioritize responses, with critical issues (severity 0–2) triggering immediate alerts, while lower levels (5–7) are archived for long-term analysis.
Facility codes identify the log source (e.g., kernel, mail, or security), enabling precise filtering and storage policies. Platforms like LogCentral leverage this grid with features such as real-time log visualization, multi-tenancy, and GDPR-compliant storage, tailored for French regulations. Mismanagement of logs can lead to missed security events, delayed responses, or fines of up to 4% of global turnover.
The syslog priority grid simplifies log management, ensuring critical events are addressed while maintaining compliance and operational efficiency.
Syslog Explained | Cisco CCNA 200-301
Syslog Severity Levels Explained
Syslog severity levels, as outlined in RFC 5424, use a reverse numbering system. This setup might seem counterintuitive at first - lower numbers signify more critical issues, while higher numbers represent less urgent scenarios. For instance, severity 0 signals the most pressing emergencies, whereas severity 7 is reserved for routine debugging details.
8 Severity Levels Overview
The eight standard severity levels serve as a structured way to classify log messages based on their impact on operations:
| Level | Severity | Keyword | Description | Real-World Example |
|---|---|---|---|---|
| 0 | Emergency | emerg | System is unusable | A complete server power failure or a kernel panic causing a full crash |
| 1 | Alert | alert | Immediate action required | Detection of unauthorised access or a firewall rule breach |
| 2 | Critical | crit | Critical conditions | RAID array failure, database downtime, or primary network outage |
| 3 | Error | err | Error conditions | Backup job failures, application crashes, or interrupted services |
| 4 | Warning | warning | Warning conditions | Disk usage exceeding 90% or high CPU usage warnings |
| 5 | Notice | notice | Normal but significant condition | System start-ups, configuration changes, or scheduled maintenance completion |
| 6 | Informational | info | Informational messages | Routine health checks, service updates, or completed backups |
| 7 | Debug | debug | Debug-level messages | Detailed application traces or variable dumps for troubleshooting |
These levels provide a clear framework for prioritising and responding to various types of log data.
How Severity Levels Work in Practice
Severity levels are essential for turning raw log data into actionable insights through automated workflows. Modern syslog management tools use these levels to create tiered response systems, ensuring that critical issues are addressed promptly while less urgent messages are handled appropriately.
For instance, IT teams typically configure monitoring systems so that messages with severity levels 0–2 trigger immediate alerts - often via SMS or other high-priority channels. Events classified as severity 3–4 might generate support tickets for review during business hours, while severity 5–7 logs are often archived for audits or long-term trend analysis.
That said, the reverse numbering system can lead to confusion. Many assume that higher numbers denote greater urgency, which can result in misconfigured alerts. This might either overwhelm teams with low-priority notifications or, worse, fail to highlight true emergencies.
Managed Service Providers (MSPs) often use severity levels to structure their service offerings. Premium support packages might guarantee immediate responses to severe incidents, while standard agreements focus only on critical events, ensuring resources are allocated efficiently.
However, misclassifying logs can lead to "alert fatigue", where teams become desensitised to notifications due to overclassification. On the flip side, underclassifying logs can delay critical responses during emergencies. Striking the right balance in severity mapping is crucial for maintaining operational effectiveness.
Severity levels also play a key role in regulatory compliance. For example, organisations in France can configure their logging systems to track security breaches (typically severity 0–2) and important system changes (often severity 5). This helps meet GDPR and other data protection requirements by ensuring that relevant events are properly logged and reviewed.
Finally, combining severity levels with facility codes allows for precise log filtering. By focusing on specific combinations - like authentication warnings and higher-severity events - organisations can reduce storage costs while still maintaining visibility into critical security issues. This approach is especially valuable when processing millions of log entries daily.
Up next, we’ll explore how facility codes work alongside severity levels to refine log categorisation even further.
Syslog Facility Codes Explained
Severity levels indicate how urgent a log message is, while facility codes identify where the message originates. This categorisation turns chaotic streams of log data into structured and manageable information.
Facility codes range from 0 to 23, with each number linked to a particular system component. For example, kernel messages use facility 0, while user-level messages are assigned facility 1. Unlike the reverse-ordered severity levels, facility codes are more intuitive, helping administrators quickly pinpoint the source of an issue.
With millions of logs generated daily, facility codes group messages by subsystem, making it easier to focus on relevant data without wading through unrelated entries. Below, we explore the most common facility codes and their practical uses.
Common Facility Codes
Facility codes cover a variety of system components and services that generate logs. Understanding these codes can help you effectively filter and route log messages.
| Facility Code | Subsystem/Application | Typical Log Source Example |
|---|---|---|
| 0 | Kernel | OS kernel events, hardware errors |
| 1 | User-level | User applications, custom software |
| 2 | Email servers like Postfix or Sendmail | |
| 3 | System daemons | Background services (cron, sshd) |
| 4 | Security/Authorisation | Authentication attempts, sudo usage |
| 5 | Syslog daemon | Internal syslog system messages |
| 10 | AuthPriv | Sensitive security events |
| 11 | FTP daemon | File transfer protocol services |
| 16–23 | Local0–Local7 | Custom application logs |
Kernel messages (facility 0) often highlight critical issues like hardware failures or driver errors. These logs demand immediate attention, as they can signal fundamental system problems.
Mail system logs (facility 2) monitor email activity, including delivery status, spam filtering, and server performance. These logs are indispensable for troubleshooting email-related issues.
System daemon logs (facility 3) track essential background services, such as SSH connections, scheduled tasks, and service start-ups. Administrators rely on these logs to ensure smooth operations.
The security-related facilities (4 and 10) are particularly important. Facility 4 captures general authentication events, while facility 10 (authpriv) is reserved for sensitive security data that requires restricted access. This separation helps organisations enforce stringent access controls for security logs.
Finally, local facilities (16–23) offer flexibility for custom applications. Businesses often assign these codes to specific software systems, ensuring clear separation between different applications.
How Facility Codes Filter Logs
Facility codes help transform raw log data into actionable insights tailored to specific operational needs.
The formula PRI = (Facility × 8) + Severity determines how messages are sorted and routed based on their source and urgency. Modern syslog platforms use facility codes to create targeted log streams. For instance, security teams can focus exclusively on authentication logs (facilities 4 and 10), while system administrators monitor kernel and daemon messages (facilities 0 and 3). This focused approach reduces information overload and speeds up response times.
In multi-tenant environments, facility codes are invaluable for separating client logs. Managed Service Providers (MSPs) can assign local facility codes to individual clients, ensuring each customer sees only their own data. This approach not only boosts operational efficiency but also supports compliance with regulations.
Facility-based filtering also optimises storage. Organisations can set retention policies by facility code - keeping security logs for extended periods while purging less critical data like debug logs. This strikes a balance between compliance and cost management.
Platforms like LogCentral take facility code usage a step further with native multi-tenancy and GDPR-compliant access controls. These features automatically route logs based on facility codes, making the system particularly suitable for French organisations with strict data protection requirements.
Advanced platforms can even trigger automatic security responses. For example, if authentication logs (facility 4) detect suspicious activity, the system can implement protective measures like blocking IPs without human intervention.
How Severity and Facility Work Together
Syslog messaging becomes most effective when severity levels and facility codes work hand in hand to create a structured priority system. This combination helps categorize logs for automated filtering, routing, and response.
This dual classification is especially useful in environments where thousands of messages are generated every minute. For instance, a critical kernel panic requires immediate action, while routine debug messages from user applications can be stored for later review. Together, severity and facility codes provide the foundation for advanced log management, which will be further explored in the next sections on priority grids and tool capabilities.
Priority Calculation Formula
Each syslog message is assigned a priority value using a simple formula:
Priority = (Facility × 8) + Severity
This calculation ensures that each facility's range is uniquely positioned within the overall priority spectrum.
Take a kernel panic as an example: facility 0 (kernel) paired with severity 0 (emergency) results in a priority value of (0 × 8) + 0 = **0** - the most critical log message, requiring immediate action. On the other hand, an authentication failure from facility 4 (auth) with severity 3 (error) calculates as (4 × 8) + 3 = **35**, signaling a significant security event but one less urgent than a kernel panic. Similarly, a debug message from user-level processes (facility 1) with severity 7 results in (1 × 8) + 7 = **15**, which is helpful for troubleshooting but not time-sensitive.
The beauty of this formula lies in its simplicity. Modern syslog systems embed this priority value directly in message headers (e.g., <35>), allowing log management tools to quickly identify the source and urgency of any message.
Severity vs Facility Comparison
Severity levels and facility codes complement each other, playing essential roles in efficient log management.
| Aspect | Severity Levels | Facility Codes |
|---|---|---|
| Numeric Range | 0–7 | 0–23 |
| Primary Purpose | Indicates urgency | Identifies log source |
| Filtering Benefits | Prioritizes response | Enables targeted routing |
Severity levels focus on urgency, ensuring that critical events receive immediate attention, regardless of their source. Facility codes, on the other hand, provide context by identifying where a log entry originates.
This combination enables powerful filtering options. For instance, administrators can set up alerts for all error messages (severity 3) from the authentication facility (facility 4) to monitor failed login attempts without being overwhelmed by less critical notifications. Similarly, logs from the mail system (facility 2) with a warning severity or higher can be routed directly to email administrators.
Facility codes also support compliance needs by enabling tailored retention policies. Security logs, such as those from facilities 4 and 10, can be stored for extended periods to meet regulatory requirements, while less critical debug-level logs can be purged regularly to optimize storage costs.
In multi-tenant setups, facility codes are crucial for maintaining log isolation across different clients. Managed Service Providers can assign local facility codes (16–23) to individual customers, ensuring proper separation. When paired with severity-based alerting, this approach enables scalable and efficient monitoring across multiple clients.
For example, platforms like LogCentral utilize this dual classification system to meet GDPR compliance needs while supporting client-specific filtering. By automatically applying French data formatting standards and retaining priority calculations, these platforms ensure efficient log processing while adhering to regulatory requirements.
Next, we’ll explore how tools like LogCentral use this classification system to deliver effective log management solutions.
Priority Grid in Log Management Tools
Building on the earlier discussion about severity levels and facility codes, modern log management tools now take these elements and weave them into a functional priority grid. These platforms transform the theoretical syslog priority grid into practical systems that automatically organise, route, and respond to log events based on their facility and severity values.
How this is implemented can vary widely between platforms, especially when it comes to features like compliance, multi-tenancy support, and localisation for French and European markets. While most tools offer basic priority filtering, enterprise-grade platforms stand out with advanced capabilities like GDPR compliance and smarter alerting systems.
LogCentral Priority Grid Features
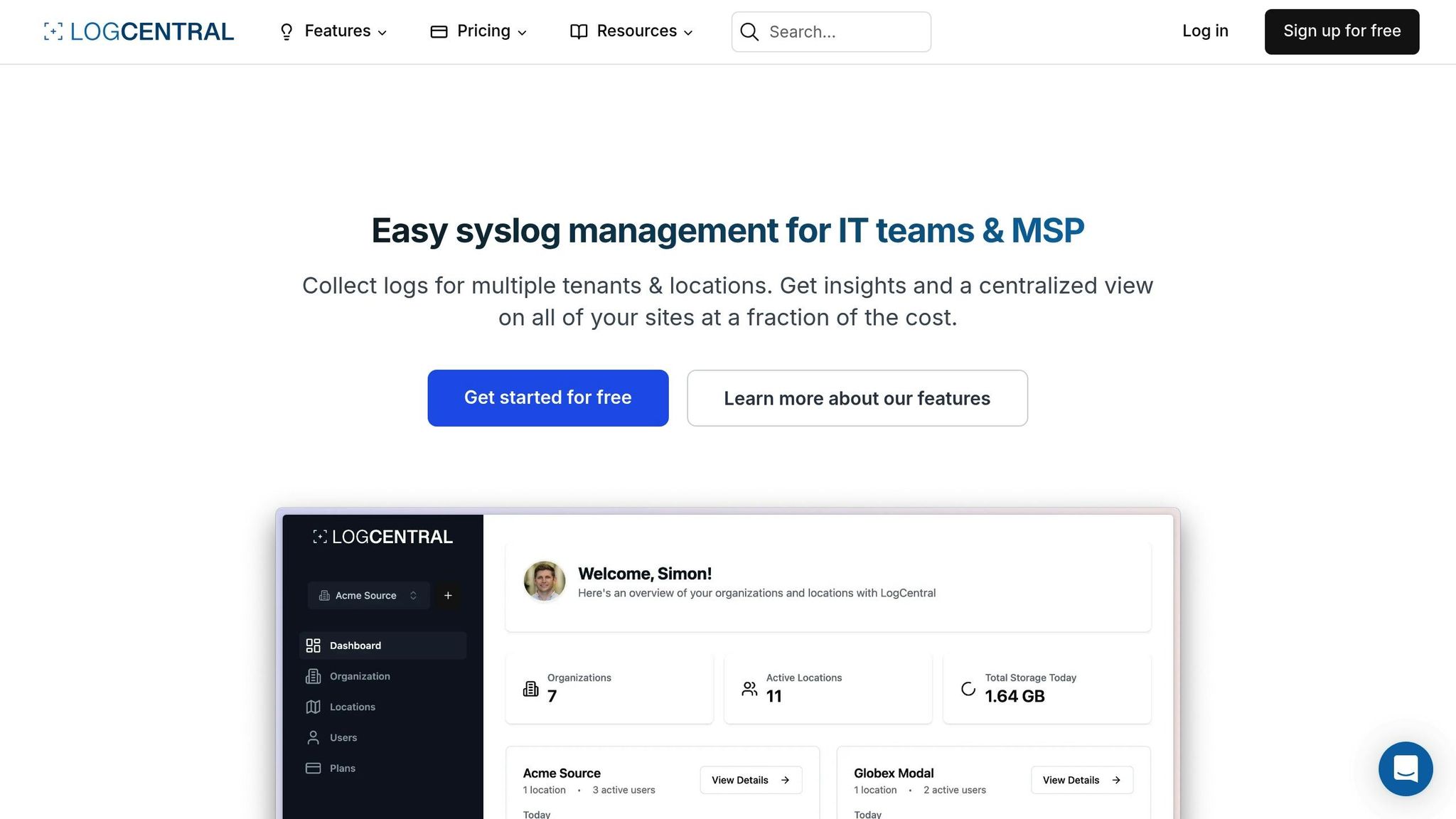
LogCentral takes the priority formula and applies it to deliver precise filtering and routing capabilities, fully adapted to French localisation standards, including date and time formats.
One standout feature is live log visualisation, which displays incoming messages in real-time. Messages are colour-coded by priority, allowing administrators to quickly spot critical events. The platform’s intelligent alerting system goes a step further, analysing priority patterns to minimise false positives. This ensures French IT teams receive meaningful alerts instead of being overwhelmed by irrelevant notifications.
With its native multi-tenancy design, LogCentral is particularly suited for managed service providers (MSPs). It enables them to create separate priority grid rules for each client while maintaining strict data isolation in line with GDPR requirements.
Long-term retention policies are another highlight. Logs related to security, such as those from authentication facilities, can be stored for extended periods to meet French regulatory requirements. Meanwhile, debug-level messages are automatically purged based on configurable schedules, balancing compliance with storage efficiency.
LogCentral also integrates automatic firewalling and smart IP management with the priority grid system. High-priority security events can trigger immediate protective actions, while lower-priority messages are simply logged for monitoring purposes.
This comprehensive approach not only addresses compliance and localisation needs but also provides a strong foundation for comparing LogCentral to other platforms.
LogCentral vs Other Platforms
LogCentral’s focus on GDPR compliance and French data standards clearly sets it apart from competitors in critical areas.
| Feature | LogCentral | SolarWinds Orion | IBM Guardium | Trend Micro | SigNoz |
|---|---|---|---|---|---|
| GDPR Compliance | Yes (EU hosted) | Partial | Yes | Partial | Partial |
| Multi-Tenancy | Native | Limited | Yes | No | No |
| Live Log Visualisation | Yes | Yes | Yes | No | Yes |
| Intelligent Alerts | Yes | Yes | Yes | Yes | Yes |
| Cisco Meraki Integration | Yes | No | No | No | No |
| Hosted in France/EU | Yes | No | Yes | No | No |
LogCentral’s GDPR compliance by default is a key advantage for French IT teams. The platform automatically applies French data formatting standards, such as using commas as decimal separators (e.g., 35,7 instead of 35.7) and metric units, while ensuring all log data stays within European borders.
The platform’s native multi-tenancy is another major strength. Unlike SolarWinds Orion, which offers limited multi-tenant capabilities requiring complicated setup, LogCentral provides built-in client separation right from installation.
For organisations using Cisco networking equipment, LogCentral’s Cisco Meraki integration is a valuable feature. It automatically maps Meraki facility codes to appropriate priority levels, simplifying network monitoring without the need for manual configuration.
LogCentral also offers transparent and scalable pricing, making it well-suited for French businesses.
While all platforms in the comparison table support real-time monitoring and intelligent alerting, LogCentral stands out by reducing alert fatigue. Instead of simply reacting to every severity 0-2 message, the system evaluates facility context and historical patterns to deliver more targeted notifications - something French administrators will appreciate.
With its combination of European hosting, built-in GDPR compliance, and French localisation, LogCentral is particularly well-suited for businesses operating under French data protection laws. Other platforms often require additional setup or third-party tools to meet these requirements, making LogCentral a more seamless option.
French Standards and Requirements
Ensuring syslog management aligns with French standards is essential for maintaining the efficiency of priority grids under local regulatory and operational conditions. When deploying syslog management tools in France, it's crucial to adapt systems to French-specific formats and regulations. French IT teams expect these tools to seamlessly integrate with national formatting standards, regulatory frameworks, and local conventions. Such precision is especially critical in managing priority grids, where errors in timestamps or data values could lead to costly operational missteps.
Let’s dive into the specific data format requirements crucial for French IT operations.
French Data Format Requirements
In France, IT systems must adhere to specific formatting rules. Dates are written in the DD/MM/YYYY format (e.g., 11/11/2025), and time is displayed in the 24-hour format. Numbers use spaces as thousand separators and commas as decimal points (e.g., 35,7%). Currency is presented as 1 000,00 €, with the euro symbol placed after the amount. Additionally, metric units are standard for measurements, including temperature (°C), storage (GB, TB), and distances (kilometres).
Maintaining these conventions is vital for accurately tracking priority trends and ensuring smooth event correlation across facilities.
In January 2024, BNP Paribas transitioned to a GDPR-compliant, EU-hosted syslog platform configured with French-specific data formats. This move reduced compliance audit findings by 30% and improved user satisfaction.
Modern syslog platforms should automatically apply these formatting rules across all reports, interfaces, and data exports. Relying on manual adjustments for every format element not only increases the risk of inconsistencies but also jeopardises operational efficiency.
These formatting standards also play a key role in meeting stringent French data protection laws, as outlined below.
GDPR and French Data Laws
Compliance with GDPR is an absolute necessity for syslog management solutions operating in France. The regulation governs how priority grids handle log data, including processing, storage, and retention.
GDPR requires that logs containing personal data remain within EU borders and only be retained for the legally mandated duration. LogCentral ensures compliance by implementing retention policies and selective data redaction. This is particularly important for logs involving authentication, user activity, and network access, which often include personally identifiable information.
LogCentral’s European hosting infrastructure and built-in GDPR framework allow for long-term retention policies tailored to French regulations. The platform also automatically deletes data exceeding legal retention periods, helping reduce compliance risks while keeping storage costs manageable.
GDPR’s principles of user consent and data minimisation further influence how syslog systems operate. Priority grids must be configured to collect only the data necessary for their function, avoiding excessive logging that could breach GDPR’s proportionality rules. LogCentral addresses this through role-based access control (RBAC), ensuring that access to logs is limited to authorised personnel based on their job responsibilities.
In 2023, CNIL, France's data protection authority, issued over 100 000 000,00 € in fines for GDPR violations, illustrating the financial consequences of poor data management[1]. Over 80% of French enterprises now require EU-hosted log management solutions to comply with both regulatory demands and internal policies[1].
The "right to erasure" adds another layer of complexity to log retention. While security logs often need to be stored long-term for compliance, personal data within those logs may need to be deleted upon request. Advanced syslog platforms address this challenge by enabling selective data redaction, which preserves the integrity of security audit trails while respecting privacy rights.
Additionally, platform interfaces must follow French linguistic norms, avoid unnecessary anglicisms, and provide comprehensive documentation in French. LogCentral’s combination of technical compliance and attention to local conventions creates a user-friendly experience for French IT teams, boosting adoption and operational efficiency.
These localisation and compliance measures aren’t just bureaucratic requirements - they directly influence the effectiveness of priority grids in real-world French environments. Proper implementation is essential for successful syslog management in France.
Summary
The syslog priority grid plays a key role in effective log management by combining severity levels (0–7) with facility codes (0–23). This structured system helps manage system messages efficiently, even in complex IT environments[1].
For French IT teams and managed service providers (MSPs) handling diverse systems, this grid is especially useful. It enables teams to set up automated alerts for critical security incidents while directing routine data to separate storage systems. This approach reduces alert fatigue and ensures faster responses to pressing issues[1].
LogCentral takes this concept further by applying the syslog priority grid in practical scenarios to offer tailored syslog management for French organisations. Its GDPR-compliant architecture, hosted in Europe, aligns with data residency requirements. The platform provides intelligent filtering, real-time visualisation, and automated alerts based on priority levels. Its multi-tenancy feature allows MSPs to manage multiple clients efficiently, offering each tenant customised routing and long-term data retention based on priority.
LogCentral also meets local standards with proper formatting and regulatory compliance. Additional functionalities like role-based access control (RBAC), seamless Cisco Meraki integration, and advanced IP management enhance operations for diverse IT teams.
FAQs
How does the syslog priority grid support GDPR compliance for IT teams in France?
The syslog priority grid is a valuable tool for IT teams in France, helping them organise log data by combining severity levels and facility codes. This method ensures that urgent issues get the attention they need, which is crucial for meeting GDPR's stringent data security and monitoring standards.
LogCentral takes this a step further with its GDPR-compliant syslog management solution, designed specifically for European businesses. It offers features like smart alerts, extended log retention, and round-the-clock monitoring, making it easier for organisations to stay compliant while maintaining strong data protection protocols.
What challenges can arise from the reverse numbering system in syslog severity levels, and how can they be addressed?
The syslog severity levels use a reverse numbering system, where lower numbers represent higher severity (e.g., 0 for Emergency and 7 for Debug). While effective in its design, this system can sometimes confuse those who are new to syslog or managing logs from multiple sources. Such misunderstandings might lead to misreading log data, which could delay addressing critical issues.
To address this challenge, it's crucial to ensure team members working with syslog receive thorough documentation and training. Additionally, leveraging a syslog management platform like LogCentral can make a big difference. These platforms provide user-friendly visualizations and tools that automatically sort logs by severity, minimizing the chances of human error. This approach ensures smoother and more reliable log management, even in complex IT setups.
What are syslog facility codes, and how do they help filter and route log messages effectively?
Syslog facility codes are used to categorize log messages based on their origin or type. This classification helps IT teams filter and direct logs to the appropriate systems more effectively. By organizing messages in this way, teams can focus on critical alerts, make log analysis more efficient, and respond to incidents faster.
LogCentral takes this a step further with its centralized syslog management platform. It offers features like native multi-tenancy, real-time monitoring, and intelligent filtering, enabling businesses of all sizes to maintain compliance and operate efficiently.