
Privileged Access Risk Mitigation: Best Practices for MSPs
Privileged Access Risk Mitigation: Best Practices for MSPs
Managing privileged access is critical for MSPs. Why? Privileged accounts are high-value targets for cyberattacks, and breaches involving these accounts can lead to devastating consequences for both MSPs and their clients. A single compromised account could impact multiple client environments, making security a top priority.
Key Takeaways:
-
Privileged Access Risks:
- 74% of organisations faced attacks involving privileged accounts in 2024.
- Multi-tenancy increases risks of cross-client data exposure.
- Compliance regulations like GDPR demand strict access controls and monitoring.
-
Best Practices:
- Access Policies: Define who can access what, under which conditions, and regularly review these rules.
- MFA: Enforce Multi-Factor Authentication to reduce unauthorised access incidents by up to 56%.
- Least Privilege Principle (PoLP): Limit access to only what's necessary for each role.
- Continuous Monitoring: Detect suspicious activities in real-time, reducing breach detection times by 45%.
-
Syslog Management:
- Centralised logging simplifies monitoring across multiple clients.
- Tools like LogCentral enable GDPR compliance, real-time alerts, and long-term log retention.
Bottom Line: For MSPs, safeguarding privileged access isn’t optional - it’s the foundation of secure operations and client trust. Implementing strong access controls, continuous monitoring, and robust logging systems ensures both compliance and security.
Backwards and Forwards, The MSP's Security Journey
Privileged Access Management Best Practices
Managing privileged access is a cornerstone of reducing risks for Managed Service Providers (MSPs). To strengthen security, MSPs need to follow certain best practices that ensure access is both controlled and monitored effectively.
Creating Clear Access Policies
Clear and formal access policies are the backbone of managing privileged access. These policies outline who can access specific resources, under what circumstances, and through which approval processes [2]. Without this structure, MSPs risk inconsistent decisions, compliance issues, and security vulnerabilities, especially in multi-tenant environments.
A well-structured access policy should include:
- Criteria for user eligibility
- Classification of resources
- Approval workflows
- Regular reviews and updates
These policies must align with GDPR standards and be available in French, reflecting local regulatory requirements. They should also define distinct access levels based on roles. For instance, junior technicians may only need limited access, while senior engineers might require broader administrative permissions.
Developing these policies involves identifying critical assets, mapping access points, and documenting the reasons for granting each privileged account [1]. This is crucial, as 74% of data breaches involve misuse of privileged credentials, according to Keeper Security [2]. With these policies in place, MSPs can enforce multi-layered authentication and reduce risks significantly.
Setting Up Strong Authentication
Multi-Factor Authentication (MFA) stands out as one of the most effective ways to protect privileged accounts. A 2024 Ponemon Institute report revealed that organisations using MFA for privileged accounts saw a 56% drop in unauthorised access incidents compared to those relying only on passwords [2]. This makes MFA indispensable for MSPs managing multiple client systems.
To strengthen authentication:
- Use a combination of passwords, tokens, and biometrics.
- Implement Time-Based One-Time Passwords (TOTPs) to generate temporary codes that expire quickly, reducing misuse opportunities [2][3].
- Complement MFA with Single Sign-On (SSO) to simplify access while maintaining security. However, ensure features like strong session management and automatic logout are included to prevent unattended workstations from becoming risks.
Time-restricted access adds another layer of security. For example, administrative privileges could be limited to business hours (9h00–18h00), with exceptions only for emergency maintenance. This approach not only reduces after-hours attack risks but also creates clearer audit trails for compliance.
Tools like LogCentral support these efforts with features such as role-based access control (RBAC) and seamless integration into existing systems. With GDPR compliance and European hosting, LogCentral meets French regulatory needs while delivering robust security capabilities [4]. Together with limiting access to essential resources, strong authentication significantly reduces vulnerabilities.
Using the Principle of Least Privilege (PoLP)
The Principle of Least Privilege (PoLP) ensures that users receive only the access they need to perform their roles - nothing more. For MSPs, this means carefully tailoring access permissions for each technician and client, avoiding blanket administrative rights across systems [2].
To implement PoLP:
- Conduct a privilege audit across all client environments.
- Use automated tools to identify excessive permissions, enforce PoLP, and detect dormant accounts with elevated access [5].
- Schedule regular automated reviews to adapt to changing roles and client requirements.
By limiting access, PoLP minimises the risks of human error and reduces the damage caused by compromised accounts. If a breach occurs, restricted privileges ensure attackers gain access to only a small portion of the system, not its entirety [2]. Just-in-Time (JIT) access further enhances security by granting temporary elevated permissions for specific tasks, reducing the attack surface.
For shared privileged accounts - though best avoided - strict controls are essential. Assign unique login credentials to each user, log all activities comprehensively, and enforce time-of-day restrictions for maintenance [1]. If shared accounts are unavoidable, robust auditing becomes critical to maintain accountability and meet compliance requirements [5].
LogCentral aids PoLP implementation with features like multi-tenancy and real-time alerts. Its live log visualisation helps MSPs spot unusual access patterns or privilege escalations quickly, enabling immediate action [4]. Combined with central logging, PoLP provides a strong framework for detecting and addressing suspicious activities promptly.
Multi-Tenancy and Compliance for MSPs
Handling multiple clients at once comes with its own set of hurdles, especially for Managed Service Providers (MSPs). Beyond the basics of access control, MSPs have to juggle data separation, regulatory compliance, and constant monitoring - all while keeping operations running smoothly across varied client setups.
Managing Multi-Tenancy Challenges
At the heart of secure multi-tenancy lies the need for strict data separation and tailored access controls for each tenant. A 2024 KPMG report revealed that over 60% of MSPs in Europe rank multi-tenancy and compliance as their biggest security concerns [3]. This makes sense given the intricate task of preventing data from one client being accessed by another, while also managing user roles and permissions at scale.
To achieve secure data separation, MSPs need to implement both logical and physical strategies. For instance, network segmentation creates clear boundaries between client environments, while role-based access control (RBAC) ensures technicians only access resources specific to their assigned clients. Take this scenario: a junior technician working on Client A's systems shouldn't be able to see or interact with Client B's infrastructure, no matter their level of access within Client A's environment.
LogCentral simplifies these complexities with its built-in multi-tenancy features. MSPs can manage multiple clients from a single platform while maintaining strict data boundaries. Tenant-specific log management ensures that each client's data remains fully isolated, and customizable access controls prevent unauthorized cross-client access.
To add another layer of security, LogCentral employs automated policy enforcement and regular audits to ensure privileged users can't overstep their boundaries. Features like smart IP management and automatic firewalling establish solid network barriers between clients, working alongside administrative rules to reduce risks of accidental or malicious data exposure.
GDPR Compliance in Privileged Access Management
For MSPs operating in France, adhering to GDPR is non-negotiable, with hefty fines awaiting those who fail to comply. GDPR emphasizes principles like data minimization, purpose limitation, and lawful data processing. It also mandates detailed logging, monitoring, and auditing of privileged access to personal data, ensuring clear records of who accessed what, when, and why.
Every administrative action, system change, or data access event must be logged in a way that supports compliance reporting. Unfortunately, many traditional logging tools fall short when it comes to the granularity and data retention needed for GDPR compliance.
LogCentral addresses these gaps with its GDPR-compliant design. Logs are securely stored within the EU, meeting data sovereignty requirements and privacy standards. Its long-term retention capabilities allow MSPs to maintain audit trails for the necessary 12 months (as required by most frameworks), ensuring the data is readily available for audits or investigations.
With hosting exclusively in Europe, LogCentral ensures that client data stays within European jurisdiction, even for backups or disaster recovery. This is especially critical for French MSPs, who must demonstrate compliance with data residency regulations. These measures integrate seamlessly with continuous monitoring strategies, adding another layer of protection for privileged access.
Continuous Monitoring and Auditing
Beyond tenant isolation and compliance, continuous monitoring plays a vital role in detecting real-time anomalies across client environments. A 2023 Gartner survey highlighted that continuous monitoring of privileged access reduces breach detection times by 45% [4].
Effective monitoring tools should flag unusual activity - like an admin trying to log in at 22:00 when access is restricted to 09:00–18:00 - or attempts to access unauthorized client data. These alerts need to be actionable, providing security teams with enough context to assess and respond quickly to potential threats.
Real-time log visualization further enhances oversight, offering MSPs insights into user actions across all clients. Patterns or anomalies that might signal a breach can be identified, while session recording ensures detailed records of privileged activities, fostering accountability.
LogCentral’s 24/7 monitoring ensures that suspicious actions are flagged no matter when they occur. Its intelligent alerting system notifies administrators immediately of unusual or potentially harmful activities, enabling swift responses across time zones and client environments.
To keep monitoring effective as roles and client needs evolve, LogCentral automates policy reviews. It quickly identifies dormant accounts with elevated access and ensures monitoring policies remain up-to-date, maintaining comprehensive oversight across all client environments.
Syslog Management Solutions for Risk Reduction
Managing privileged access risks effectively calls for a centralised syslog management system. By turning scattered log data into actionable insights, such systems strengthen threat detection and compliance measures. Without centralised logging, MSPs face significant challenges in maintaining security oversight. The right platform can bridge this gap, offering the tools MSPs need to safeguard their operations.
Let’s dive into how centralised logging simplifies risk management and integrates seamlessly with broader security practices for MSPs.
Why Centralised Logging Matters
Centralised syslog management allows MSPs to collect, analyse, and monitor privileged access events across all client environments from a single, unified interface. This consolidated approach makes it easier to detect unusual patterns that might otherwise remain hidden in isolated systems.
According to Ponemon Institute's 2023 data, organisations using centralised log management reduce breach detection times by up to 50% compared to those without such systems. For MSPs managing multiple client environments, this time-saving advantage can be the difference between containing a threat and dealing with a full-scale security breach.
Centralised logging also enhances anomaly detection. For example, if a privileged user attempts to access resources outside their usual scope, the system can flag this immediately by comparing the activity against established baselines. This cross-client visibility is crucial for MSPs, as a breach in one client environment could cascade into others.
Incident response is another area where centralised platforms shine. Instead of juggling multiple systems and manually piecing together events, administrators can investigate threats from one dashboard. This streamlined process is invaluable during high-pressure situations when every second counts.
Platform Comparison
Choosing the right syslog management platform is critical for mitigating privileged access risks. Here's a comparison of leading solutions, highlighting features that matter most to MSPs:
| Platform | Multi-Tenancy | GDPR Compliance | Live Monitoring | Intelligent Alerts | Cisco Meraki Integration | Hosting Location | RBAC | Pricing (€/month) |
|---|---|---|---|---|---|---|---|---|
| LogCentral | Native | Full | Yes | Yes | Native | Europe | Yes | Quote |
| Splunk | Limited | Partial | Yes | Yes | No | Global | Yes | ~150+ |
| Graylog | Enterprise Only | Partial | Yes | Yes | No | Global | Yes | ~80+ |
For MSPs in France, hosting location plays a key role due to GDPR's data residency rules. LogCentral's European hosting ensures all log data stays within EU jurisdiction, simplifying compliance and reducing regulatory risks. In contrast, platforms with global hosting may store data across various regions, complicating GDPR adherence.
Another standout feature is native multi-tenancy, which LogCentral offers as a built-in capability. Unlike other platforms where this feature may require additional licensing or complex configurations, LogCentral simplifies client data separation without extra costs or effort.
For MSPs invested in Cisco's ecosystem, Cisco Meraki integration is a game-changer. LogCentral's native support eliminates the need for third-party tools or custom connectors, reducing complexity and improving reliability in the logging process.
LogCentral Features for MSPs
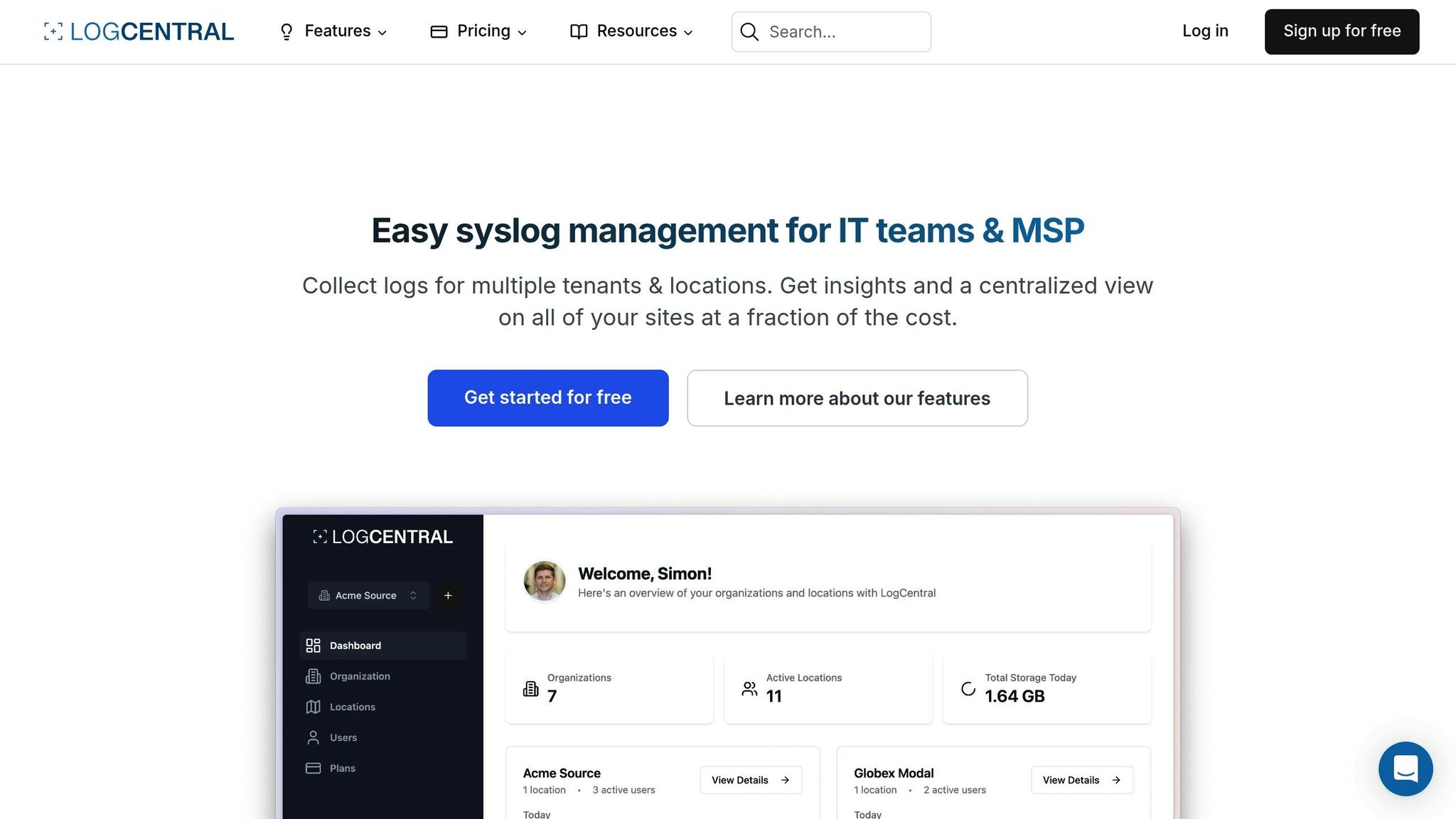
LogCentral addresses the unique challenges MSPs face in managing privileged access across diverse client environments. Its live log visualisation feature provides real-time insights, allowing security teams to identify anomalies as they happen rather than during routine reviews hours or days later.
The platform's intelligent alerting system goes beyond basic thresholds. It analyses patterns in privileged access behaviour and flags deviations that could signal a compromise or policy violation. For instance, if an administrator who typically logs in during the day accesses systems late at night, the system generates an alert for immediate review.
Additional features like automatic firewalling and smart IP management offer extra layers of network protection. If suspicious activity is detected, the platform can automatically block problematic IP addresses or restrict network access, containing threats while security teams investigate.
Long-term retention capabilities ensure compliance with GDPR's requirement to maintain audit trails for at least 12 months. This feature also supports forensic investigations, providing access to historical data that might be critical for understanding complex security incidents.
Finally, 24/7 monitoring ensures that threats are detected regardless of when they occur. IBM’s 2023 Cost of a Data Breach Report highlights that breaches involving privileged credentials cost an average of €4.45 million, making continuous monitoring a vital part of risk management. For MSPs operating across time zones or offering round-the-clock services, this ensures that anomalies are flagged immediately, even during off-hours.
These features collectively provide MSPs with the tools needed to manage privileged access risks effectively in multi-tenant environments, reinforcing their overall security posture.
Key Takeaways
This section wraps up the strategies discussed earlier, focusing on the steps Managed Service Providers (MSPs) should take to safeguard privileged access. Protecting privileged credentials isn't just about security - it's about maintaining client trust. The measures outlined here act as a strong defense against the increasingly sophisticated threats targeting these accounts.
Best Practices Summary
Privileged access management (PAM) comes with its own challenges, including multi-tenancy and GDPR compliance. To tackle these effectively, MSPs should focus on four essential pillars:
- Inventory and Multi-Factor Authentication (MFA): Start by identifying all privileged accounts across client systems. Then, enforce MFA for administrative access. According to IBM's 2024 report, breaches involving compromised credentials cost an average of €4.45 million - MFA is a crucial safeguard.
- Principle of Least Privilege: Regularly review and adjust access rights. Revoke permissions promptly when roles change, and use automated tools to catch excessive privileges. This minimizes the attack surface and limits damage from potential breaches.
- Continuous Monitoring and Auditing: Real-time visibility is key. Organisations with well-established PAM systems report up to 50% fewer incidents involving privileged accounts compared to those with less structured approaches[1].
- Clear Access Policies: Define who gets privileged access and under what circumstances. Regularly update these policies to reflect new threats and business needs.
Benefits of Effective Syslog Management
Centralised syslog management is a game-changer for MSPs, especially within France's regulatory landscape. GDPR compliance becomes more achievable with a logging solution that ensures long-term, tamper-proof data retention and supports data sovereignty through European hosting.
LogCentral stands out with its built-in multi-tenancy, eliminating the need for complex configurations or costly enterprise licenses. This feature simplifies client data management while maintaining strict security boundaries.
Operationally, the benefits go beyond compliance. Centralised logging provides immediate visibility into privileged access activities across diverse infrastructures. For MSPs using Cisco, LogCentral’s native Meraki integration removes the hassle of third-party tools, offering features like automatic firewalling and smart IP management. These tools respond to threats in real time, ensuring comprehensive protection.
Round-the-clock monitoring is another critical advantage. For MSPs serving clients across time zones or offering 24/7 services, this ensures immediate detection of threats. With breaches involving privileged credentials averaging €4.45 million in damages, continuous monitoring is not just a precaution - it’s a necessity.
FAQs
How can MSPs manage privileged access securely while complying with GDPR across multiple client environments?
To maintain secure privileged access and align with GDPR requirements across various client environments, MSPs need solutions designed for multi-tenancy and strong security measures. A tool like LogCentral makes this task more manageable by offering built-in multi-tenancy, allowing MSPs to oversee logs from multiple clients within a single, centralised platform.
Key features such as intelligent alerts, long-term data retention, and role-based access control (RBAC) ensure sensitive information remains protected and access is strictly managed. Moreover, LogCentral's GDPR compliance simplifies regulatory adherence, offering reassurance to both MSPs and their clients.
What are the best practices for applying the Principle of Least Privilege (PoLP) in a multi-tenant environment?
Implementing the Principle of Least Privilege (PoLP) in a multi-tenant environment demands thoughtful planning to maintain security without making usability a nightmare. The core idea is simple: give users and systems only the permissions they need to do their jobs - nothing extra. And don’t stop there - permissions need regular reviews and adjustments to keep up with changing roles or requirements.
In multi-tenant setups, role-based access control (RBAC) is a smart way to manage permissions. By assigning granular access based on specific roles, you can ensure tenants remain isolated, and sensitive data is only available to those who are authorised. Tools like LogCentral make this process easier by offering built-in RBAC features and advanced user management capabilities, tailored for multi-tenancy.
Another essential step is keeping a close eye on privileged access. Continuous monitoring and auditing are key here. Solutions that offer 24/7 monitoring, intelligent alerts, and detailed log visualisation, such as LogCentral, can help you catch unusual activity early and stay compliant with regulations like GDPR. Pair these measures with regular training for your team, and you’ll be in a strong position to minimise risks tied to privileged access in multi-tenant systems.
Why is continuous monitoring vital for MSPs in managing privileged access risks?
Continuous monitoring plays a key role in effective security management for Managed Service Providers (MSPs), especially when it comes to managing risks tied to privileged access. It provides real-time insights into systems, allowing MSPs to spot unusual activity or potential breaches early, before they turn into major problems.
Taking a proactive stance enables MSPs to act quickly against threats, minimising damage and protecting critical data. Tools like LogCentral make this easier by offering centralised log management with features such as multi-tenancy support, smart alerts, and long-term log storage. These capabilities help MSPs maintain strong oversight across multiple client environments.