
Log Retention Rules for Industry Compliance
Log Retention Rules for Industry Compliance
Log retention is key for compliance, security, and audits. Different industries have specific rules for how long logs must be kept. Here’s a quick breakdown:
- Healthcare (HIPAA): Logs must be retained for 6 years to protect patient data.
- Finance (SOX): Financial records require 7 years of retention, while PCI DSS mandates 12 months for cardholder data, with 3 months readily accessible.
- E-Commerce (GDPR & NIS 2): GDPR focuses on minimizing data retention, while NIS 2 requires 18 months for security logs.
Failing to follow these rules can lead to fines, data breaches, and compliance issues. Proper log management, such as using automated tools, tamper-proof storage, and regular reviews, ensures compliance and strengthens security.
Quick Comparison
| Industry | Regulation | Retention Period | Key Requirements |
|---|---|---|---|
| Healthcare | HIPAA | 6 years | Secure, tamper-proof storage; regular reviews |
| Finance | SOX | 7 years | Long-term storage for audits |
| Finance | PCI DSS | 12 months (3 months accessible) | Track access, admin actions, and changes |
| E-Commerce/General | GDPR | Varies | Justify retention; prioritize data minimization |
| E-Commerce/General | NIS 2 | 18 months | Security, access, and admin log retention |
To simplify compliance, solutions like LogCentral offer automated tools tailored to these requirements, ensuring logs are securely stored, reviewed, and retained for the required duration.
Log Retention Requirements by Industry and Regulation
PCI v4.0 - 10.5.1: Retain Audit Log History for At Least 12 Months
Healthcare (HIPAA) Log Retention Requirements
Healthcare organisations must maintain audit trails that comply with HIPAA standards for Protected Health Information (PHI). These audit trails should capture details like user identifiers, timestamps, access attempts, data modifications, and other security-related events.
6-Year Retention Period for Protected Health Information (PHI)
Under HIPAA §164.316(b)(2)(i), healthcare organisations are required to retain audit logs for six years. This guideline, supported by NIST SP 800-66, mandates comprehensive logging of both successful and failed actions across systems handling PHI [1][2]. To meet this requirement, organisations should establish a written policy outlining retention periods and procedures for secure log disposal. Additionally, some French healthcare providers may need to comply with stricter national regulations that require longer retention periods [2].
However, retention alone isn’t enough - ensuring the integrity of these logs is just as important.
Tamper-Proof Storage Requirements
HIPAA mandates that audit logs must be stored in a way that prevents tampering. Systems managing electronic health information must ensure that logs cannot be altered, overwritten, or deleted [3]. To meet this requirement, organisations can implement:
- File Integrity Monitoring: Tracks and alerts on any changes to log files.
- Real-Time Event Forwarding: Sends log data to a secure central repository.
- Encryption and Access Controls: Ensures only authorised personnel can access or manage logs.
"Audit logs serve as your organisation's digital witness, providing undeniable evidence of compliance and enabling rapid response to security incidents" [3].
With healthcare ranking as the third-most targeted industry for ransomware attacks [3], these safeguards are critical to protecting sensitive log data.
Once logs are securely stored, regular reviews are essential to maintain compliance.
Regular Log Reviews
The HIPAA Security Rule's Administrative Safeguards (§164.308(a)(1)(ii)(D)) require healthcare organisations to set up procedures for regularly reviewing audit logs and system activity records [4]. These reviews should be carried out using automated alerts and assigned personnel to identify unauthorised access or unusual activities. This proactive approach ensures compliance and helps avoid penalties, which can range from €95 to €47,500 per violation [4].
"Essentially, audit logs are the data points, and an audit trail is the story they tell when connected" [4].
Using a Security Information and Event Management (SIEM) system can simplify this process. SIEM tools centralise logs from various sources - like electronic health records, laboratory systems, and firewalls - into one secure repository. This not only streamlines the review process but also strengthens the organisation's overall compliance framework, aligning with the retention and security standards outlined above.
Finance (PCI DSS and SOX) Log Retention Requirements
Financial institutions are required to comply with PCI DSS for safeguarding cardholder data and SOX for maintaining financial systems' integrity. Both frameworks have specific rules for log retention.
PCI DSS: 12-Month Retention for Cardholder Data
Under PCI DSS, organisations must retain audit logs for at least 12 months, with the most recent three months readily accessible for real-time analysis. These logs are essential for tracking critical events, such as:
- User access to cardholder data
- Actions by administrators
- Access to audit trails
- Unsuccessful login attempts
- Modifications to logging (e.g., deletion, pausing, or stopping)
Each log entry should include details like the event type, date and time, success or failure status, event origin, and the identity of the affected system component. To ensure accuracy, system clocks must be synchronised using NTP, and unique usernames should replace shared accounts. Daily log reviews are essential for spotting irregularities [5].
While PCI DSS focuses on monitoring recent activity, SOX takes a longer-term approach to ensure financial accountability.
SOX: 7-Year Retention for Financial Systems
The Sarbanes–Oxley Act (SOX) requires financial institutions to retain audit logs for seven years. This extended retention period supports detailed audits and legal inquiries.
To navigate these differing requirements, many organisations rely on a tiered storage approach:
- Hot storage (0–90 days): Quick access for real-time monitoring
- Warm storage (90 days–1 year): Retained for incident investigations
- Cold storage (1–7 years): Meets SOX's long-term retention needs
This multi-layered strategy helps institutions comply with both standards while managing storage costs effectively.
E-Commerce and General Log Retention (GDPR and NIS 2)
E-commerce businesses face the challenge of aligning two distinct frameworks: GDPR's focus on data minimisation and NIS 2's emphasis on security retention. Both must be adhered to simultaneously, despite their differing approaches to log retention.
GDPR: Balancing Data Minimisation and Retention
Under GDPR, there are no fixed rules for how long logs should be kept. Instead, the regulation enforces Storage Limitation - keeping data only as long as necessary - and Data Minimisation - collecting only the essential information [6]. This means businesses must justify why each log is retained and ensure it’s deleted once its purpose is fulfilled. For instance, logs should only be retained if absolutely necessary under GDPR guidelines.
However, GDPR’s Article 17, often referred to as the "Right to Erasure", is not without exceptions. Retention of data is still allowed when required by legal obligations, such as compliance with security regulations like NIS 2.
To meet GDPR requirements while maintaining data security, techniques like IP masking, hashing, and pseudonymisation can be employed. These methods limit exposure to personal data while retaining the forensic value of the logs. For those aiming to retain logs indefinitely - for instance, for security trend analysis - true anonymisation is key, as it removes the data from GDPR’s scope entirely.
NIS 2: Mandatory 18-Month Retention Rule
The NIS 2 Directive enforces an 18-month minimum retention period for security, access, and administration logs across all relevant systems [7]. This rule applies to "essential" and "important" entities, typically medium-sized and large organisations with 50+ employees or a turnover of €10 million or more [8]. According to ISMS.online:
"NIS 2's 18-month log retention rule is a legal floor every 'essential' and 'important' entity must obey - regardless of industry, size, or country" [7].
Logs must be stored in a tamper-evident format and be readily exportable for audits. The directive requires tracking key events such as authentication attempts, privilege escalations, configuration changes, and other security-related activities. Mark Sharron, Search & Generative AI Strategy Lead at ISMS.online, highlights:
"Your compliance is defined by the shortest (and weakest) link in your log and evidence chain" [7].
To ensure compliance and avoid unnecessary data accumulation, automated lifecycle management can be used to purge logs after the mandatory 18-month period. This approach not only aligns with NIS 2 but also complements any industry-specific requirements, creating a structured and efficient log retention process. For more insights on managing your data, visit our LogCentral Blog for the latest in observability and monitoring.
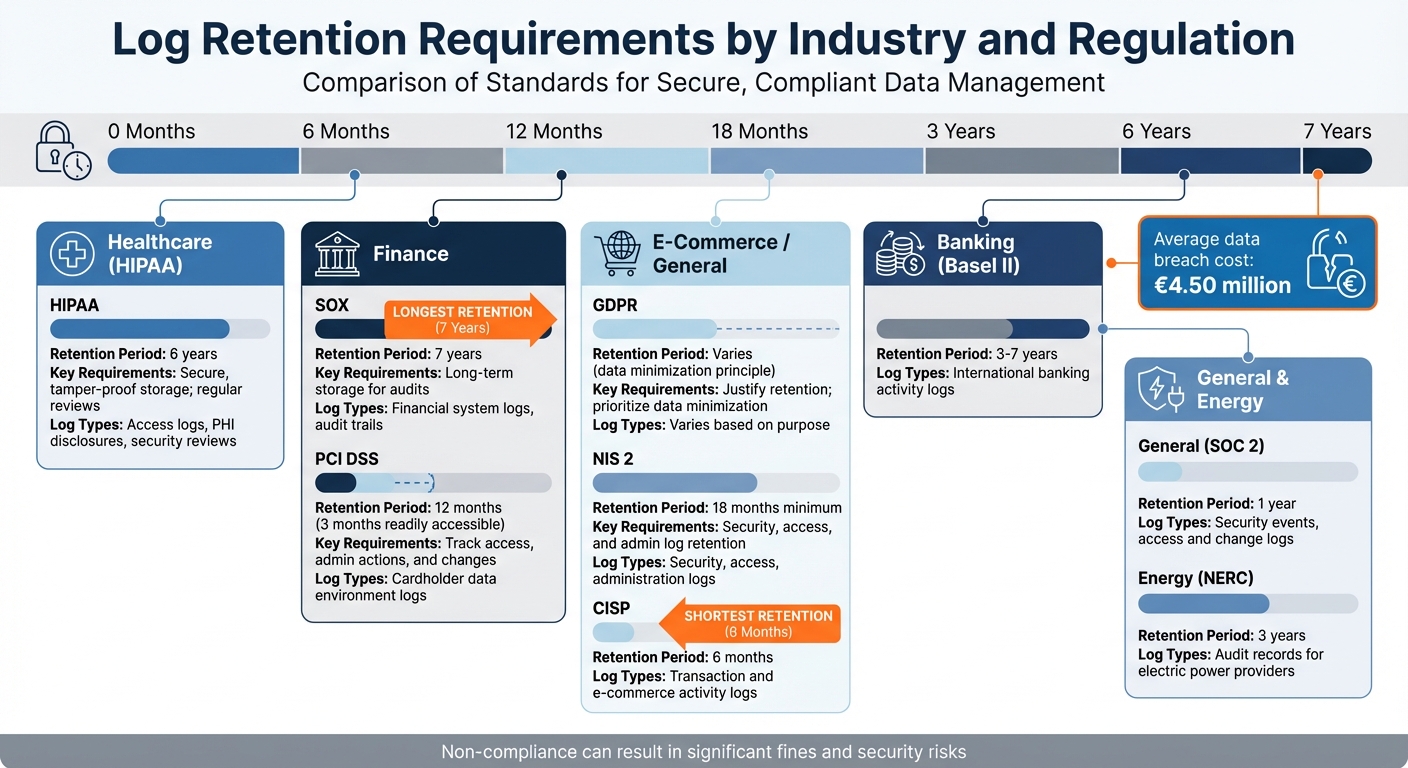
Log Retention Periods by Industry
The following checklist highlights the various retention requirements mentioned earlier.
Different industries face distinct log retention rules, driven by their specific risks and regulatory landscapes. For example, healthcare organisations must juggle patient privacy with the need for long-term audit trails, while financial institutions deal with overlapping mandates. Meanwhile, e-commerce businesses must align GDPR's data minimisation principles with stricter retention rules like those in NIS 2.
Retention timelines differ across industries: HIPAA sets a 6-year requirement, SOX mandates 7 years, and PCI DSS requires 12 months, with 3 months of logs needing to be immediately accessible. Energy providers under NERC must retain audit records for 3 years [10]. SOC 2 compliance typically involves keeping security event logs for 1 year [11].
Retention Period Comparison Table
| Regulation | Industry | Primary Log Types | Retention Period |
|---|---|---|---|
| HIPAA | Healthcare | Access logs, PHI disclosures, security reviews | 6 years [9][10] |
| SOX | Finance | Financial system logs, audit trails | 7 years |
| PCI DSS 4.0 | Finance | Cardholder data environment logs | 12 months (3 months immediately available) |
| NIS 2 | General (Essential/Important Entities) | Security, access, administration logs | 18 months minimum |
| Basel II | Banking | International banking activity logs | 3–7 years [10] |
| CISP | E-Commerce | Transaction and e-commerce activity logs | 6 months [10] |
| SOC 2 | General | Security events, access and change logs | 1 year [11] |
| NERC | Energy | Audit records for electric power providers | 3 years [10] |
This comparison table highlights the importance of a customised log management strategy, such as the solutions offered by LogCentral, to meet each industry’s specific demands.
State-level regulations can further complicate compliance. For instance, while HIPAA sets a federal standard of 6 years, hospitals in North Carolina must retain records for 11 years, and those in Texas for 10 years [9][12]. Multi-state providers must adhere to the strictest applicable standard.
Non-compliance can lead to hefty penalties, with the average cost of a data breach reaching approximately €4.50 million [10]. David Harrison, Chief Audit Executive at Origin Bank, explains the value of robust log retention:
"The external auditors for our organisation have found the audit log very helpful. They can find dates when a control has been modified and the effective date for that control and have all the parties work off the same process narrative." [10]
How LogCentral Supports Compliance and Retention
LogCentral simplifies compliance with industry-specific log retention rules, ensuring organisations meet their regulatory obligations without unnecessary complexity. Compliance isn't just about adding more storage - it's about combining long-term retention, strong security measures, and automated processes. Designed for regulated industries across France and Europe, LogCentral offers features tailored to help organisations navigate stringent requirements.
Long-Term Retention and GDPR Compliance
LogCentral ensures all logs are stored within European data centres, adhering to GDPR and CNIL regulations. The platform allows organisations to set retention periods tailored to specific regulations - such as 12 months for PCI DSS, 6 years for HIPAA, and 7 years for SOX. Automated lifecycle management prevents indefinite storage, which can lead to regulatory penalties. For example, in June 2023, the CNIL fined Criteo €40 million for GDPR violations related to data transparency, and Yahoo Ltd. faced a €10 million fine in early 2024 for cookie preference non-compliance [14].
To secure data, LogCentral uses AES-256 encryption for stored logs and TLS 1.3 for data in transit, meeting France's strict security standards. For logs retained beyond their original purpose - such as for historical analysis - the platform offers irreversible anonymisation. This removes data from GDPR's scope while preserving its analytical usefulness. As Tilman Harmeling, Senior Privacy Expert at Usercentrics, explains:
"To be prepared in case of an audit by data protection authorities, businesses should ensure they securely maintain updated and accessible records of their data collection and processing" [13].
Multi-Tenancy and 24/7 Monitoring
With multi-tenancy, MSPs and large enterprises can manage multiple clients or departments from a single dashboard while keeping data strictly isolated - a key PCI DSS requirement. Role-Based Access Control (RBAC) ensures users only access data relevant to their responsibilities, maintaining security and compliance.
LogCentral also provides 24/7 monitoring and intelligent alerting for real-time threat detection. By automating event monitoring, the platform minimises errors and ensures compliance with PCI DSS's 12-month retention rule, with 3 months of logs readily accessible. IT teams can also schedule audit-ready reports directly from the unified dashboard, reducing the workload during annual compliance reviews. Additionally, seamless hardware integration enhances overall compliance efforts.
Cisco Meraki Integration and European Hosting
For organisations using Cisco Meraki infrastructure, LogCentral offers seamless integration to capture syslog events from all devices (MX, MR, MS, MV, MG, or MT) as they leave the network. A guided wizard simplifies the setup process, enabling configuration of the Meraki Dashboard and provisioning of endpoints in under five minutes. Businesses can import all Cisco Meraki networks simultaneously with the Enterprise plan, ensuring consistent compliance across their operations.
European hosting guarantees data sovereignty, eliminating the legal risks tied to transferring data to US-based providers - an issue highlighted by CNIL enforcement actions. LogCentral also strengthens security with automatic firewalling and smart IP management, ensuring uptime and compliance continuity. This managed SaaS model removes the need for local infrastructure upkeep, allowing IT teams to focus on broader security priorities instead of server maintenance.
Conclusion
Managing log retention is a balancing act between regulatory compliance and operational efficiency. For example, healthcare organisations must retain audit logs for 6 years under HIPAA to monitor PHI (Protected Health Information) access. In contrast, financial institutions face dual requirements: 12 months for PCI DSS cardholder data (with 3 months readily accessible) and 7 years for SOX compliance regarding financial systems. Meanwhile, e-commerce businesses must adhere to GDPR's data minimisation principles, often opting for shorter retention periods based on risk assessments. Additionally, NIS 2 regulations demand a minimum of 18 months for security incident logs. These requirements reflect the specific risks and accountability standards of each industry.
Improper management of these retention timelines can lead to serious consequences. Non-compliance not only risks hefty fines but also compromises security, as insufficient retention can hinder audits, breach investigations, and forensic analysis. On the other hand, storing logs indefinitely brings its own challenges - higher costs, GDPR violations, and unnecessary data exposure. A risk-based approach offers a practical solution, such as retaining high-risk ePHI logs for the full 6 years while applying shorter retention periods to less critical operational logs, guided by a thorough risk analysis.
To simplify these complexities, LogCentral provides a comprehensive, automated solution. Its automated lifecycle management aligns retention policies with regulatory standards. The platform ensures log integrity with tamper-proof WORM storage and SHA-256 cryptographic hashing, while AES-256 encryption and TLS 1.3 secure data both at rest and in transit. Hosting within Europe guarantees compliance with CNIL and GDPR, avoiding cross-border data transfer issues and maintaining sovereignty for French and EU organisations.
For MSPs and enterprises juggling multiple clients or departments, LogCentral's native multi-tenancy ensures strict data isolation, while RBAC (Role-Based Access Control) limits access to relevant logs. Real-time 24/7 monitoring and intelligent alerts quickly identify compliance issues, and seamless Cisco Meraki integration automates log collection across network devices. By adopting this managed SaaS platform, IT teams are freed from infrastructure maintenance, allowing them to focus on more strategic tasks. LogCentral effectively supports all regulatory requirements with its integrated log management capabilities.
FAQs
What retention rule applies if I’m subject to multiple regulations?
When different regulations overlap, it's crucial to adhere to the one with the longest retention period or the strictest requirements. This approach helps ensure you meet all applicable standards at the same time. Double-check industry-specific rules to steer clear of potential compliance issues.
How can I keep logs tamper-proof without making them hard to access for audits?
To keep logs secure and tamper-proof, cryptographic techniques such as digital signatures and hashing are essential. These methods help maintain log integrity and quickly flag any unauthorized alterations. Storing logs in secure, write-once or append-only systems adds another layer of protection, ensuring that changes cannot be made retroactively.
Access to logs should be tightly controlled using role-based access controls (RBAC), limiting who can view or modify them. Pair this with continuous monitoring to detect and respond to suspicious activity in real time.
For a streamlined approach, tools like LogCentral can make compliance easier. They provide features like secure long-term storage, live log visualization, and intelligent alerts, keeping your logs safe, accessible, and fully prepared for audits.
How do I stay GDPR-compliant when security rules require longer log retention?
To ensure compliance with GDPR while meeting extended log retention requirements, set retention periods that align with legal obligations. Once personal data is no longer necessary, make sure it is securely deleted. Tools like LogCentral can simplify this process by automating retention policies, managing deletions, and maintaining audit trails. This approach supports GDPR’s right to erasure while addressing industry-specific regulations - like the French tax law mandate to retain financial logs for six years. Regularly revisiting and updating these policies is key to staying compliant.