
GDPR Compliance: Log Data Retention and Disposal
GDPR Compliance: Log Data Retention and Disposal
Managing log data under GDPR is a balancing act. You need to keep logs long enough for security, audits, and legal obligations but not a moment longer than necessary. Non-compliance can lead to hefty fines, loss of customer trust, and legal claims. Here's the key takeaway:
- Retention Rules: Define clear purposes for log data, limit retention to what's necessary, and delete data securely once its purpose is fulfilled.
- Automation: Tools like LogCentral simplify GDPR compliance with features like automated retention policies, client-side data masking, and secure deletion methods.
- Backup Challenges: Ensure deletions extend to backups and distributed systems. Use encryption and retention policies to manage these complexities.
- Audit Readiness: Maintain thorough documentation, such as a Records of Processing Activities (RoPA), and conduct regular compliance audits.
- Third-Party Oversight: Vet vendors handling your log data and include audit rights in contracts to ensure they meet GDPR standards.
Bottom line: Automating log management and maintaining proper documentation are critical to staying GDPR-compliant while meeting operational needs.
Getting started with GDPR compliance: Records of processing activities
GDPR Requirements for Log Data Retention
When it comes to GDPR compliance, handling log data isn't just about storing it securely. It’s about aligning with three key principles: purpose limitation, data minimisation, and storage limitation. These principles require organisations to define why they collect log data, limit the data to what's strictly necessary, and delete it as soon as its purpose is fulfilled. This framework ensures that all log data is treated responsibly and transparently, as explained below.
Purpose Limitation and Data Justification
Before collecting or retaining any log data, organisations need to establish specific, well-documented objectives. Vague reasons like "for security purposes" won’t cut it. Instead, objectives should be precise - think along the lines of fraud detection, regulatory compliance, or incident response.
Under Article 30 of GDPR, organisations are required to maintain a Records of Processing Activities (ROPA). This document maps out each log's purpose, the legal basis for its collection, and its retention period. For organisations in France, adherence to CNIL guidelines is essential, and this documentation must be ready for regulatory audits.
The legal basis for data retention is equally important. For instance, logs kept for tax compliance must align with French statutory retention periods. On the other hand, logs retained under "legitimate interests" (like security monitoring) demand a clear justification to prove that the retention period is both necessary and proportionate. The Article 29 Working Party provides further clarity here:
Performance of contract does not apply to actions triggered by non-compliance or to all other incidents in the execution of a contract, but only covers the normal execution of a contract [1].
Storage Limitation and Retention Periods
GDPR doesn’t set standard retention periods, leaving organisations to determine appropriate timeframes based on operational and legal requirements. The rule is simple: keep data only as long as it’s necessary for its intended purpose.
A tiered retention strategy often works best. For example, logs used for active monitoring might have shorter retention periods, while those required for audit purposes could be stored longer. French organisations should also be mindful that elements like IP addresses, user IDs, session tokens, and timestamps are considered personal data when they can indirectly identify individuals. This means they fall under GDPR’s protective umbrella and must be treated accordingly.
Creating a Log Data Retention and Disposal Strategy
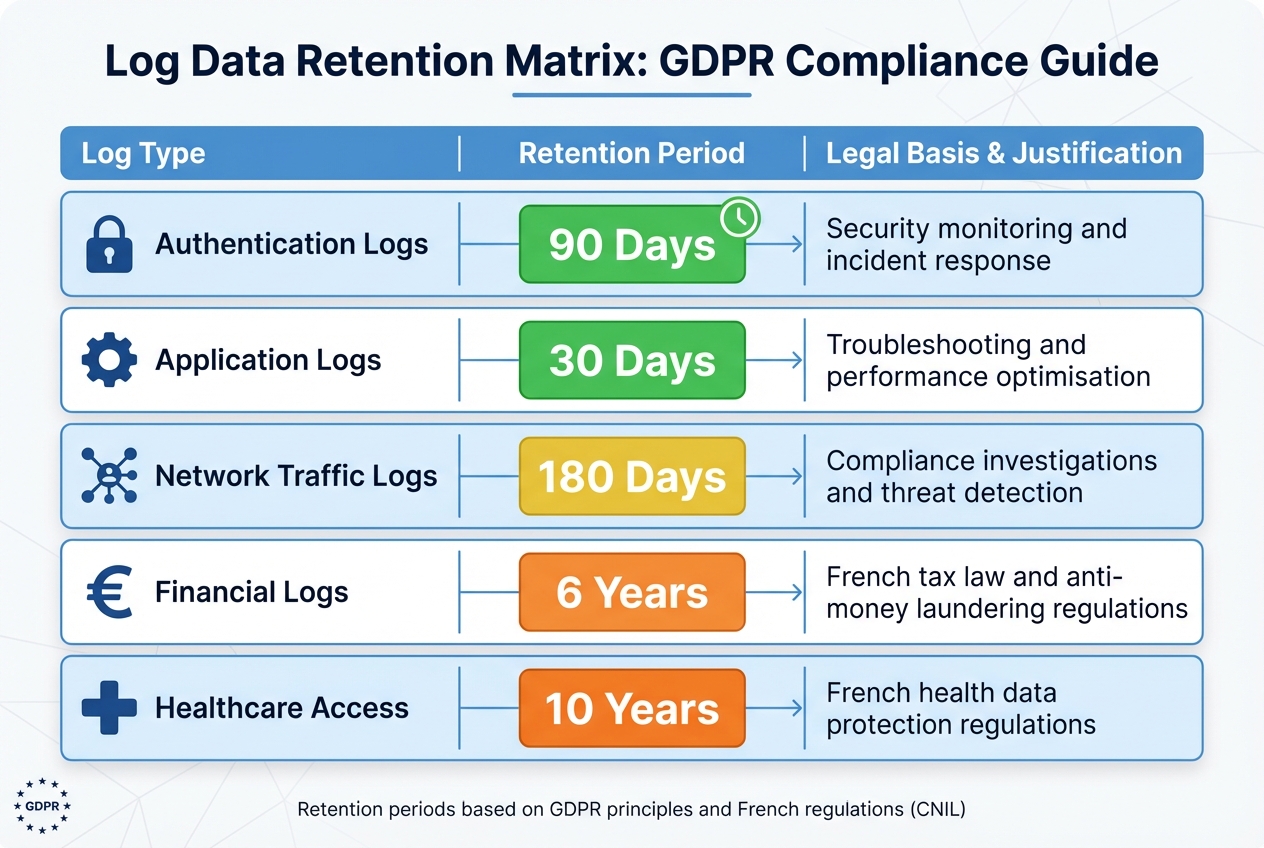
GDPR Log Data Retention Periods by Type
To align with GDPR's principles of data minimisation and storage limitation, it's essential to design a strategy that categorises log data, defines clear retention periods, and ensures secure deletion. This involves creating a data retention matrix that links each type of log to its legal basis, business purpose, and specific retention timeframe. This matrix serves as the backbone for automating log lifecycle management and meeting regulatory requirements. Below, we'll explore how to categorise logs, establish deletion triggers, and securely dispose of data.
Categorising Log Data and Setting Deletion Triggers
Logs should be categorised based on their purpose and sensitivity. For example, French regulations require a six-year retention period for financial logs and a ten-year retention period for healthcare-related access logs. The table below provides examples of log types, their retention durations, and justifications:
| Log Type | Retention Period | Legal Basis & Justification |
|---|---|---|
| Authentication Logs | 90 Days | Security monitoring and incident response |
| Application Logs | 30 Days | Troubleshooting and performance optimisation |
| Network Traffic Logs | 180 Days | Compliance investigations and threat detection |
| Financial Logs | 6 Years | French tax law and anti-money laundering regulations |
| Healthcare Access | 10 Years | French health data protection regulations |
Deletion triggers should be clearly defined, such as the end of a retention period, withdrawal of user consent, or a "Right to Erasure" request under GDPR Article 17. Automating these triggers reduces the risk of human error and ensures consistent compliance. Additionally, maintaining a suppression list of individuals who have exercised their right to erasure prevents accidental reintroduction of their data into systems. To avoid fraudulent requests, always verify the identity of the individual before processing deletion requests.
With these triggers in place, the next step is to ensure data is securely disposed of.
Secure Disposal Methods for Log Data
Standard file deletion isn't enough to meet compliance requirements. Instead, use methods like secure wiping or cryptographic erasure to ensure data cannot be recovered. For organisations using tiered storage systems, implement a clear transition process: logs should move from hot storage (active, high-performance systems) to warm storage (lower-cost, periodic access systems) and finally to cold storage (low-cost, compressed archives) before being securely deleted.
Backup systems present a unique challenge, as immediate deletion is often not feasible. In such cases, isolate and encrypt the backups to make the data unusable for operational purposes. This approach satisfies GDPR requirements by ensuring that the data, while still physically present, is inaccessible until the backup cycle overwrites it. To maintain accountability, document all deletion actions, including details of what was deleted, when it occurred, and who authorised the action. This audit trail is critical for compliance with regulators like the CNIL.
LogCentral simplifies these processes by automating retention and deletion according to CNIL guidelines. The platform offers features such as automated retention (defaulting to 6 months, configurable up to 12 months), client-side data masking, and seamless archive management. Logs are automatically transitioned through storage tiers, and secure deletion is performed once retention periods expire. With data hosted in France on EU-compliant infrastructure, LogCentral allows organisations to focus on their core activities while ensuring GDPR-compliant log management is handled efficiently.
Managing Log Data in Backups and Distributed Systems
Backups and distributed systems add layers of complexity when it comes to GDPR compliance. Deleting log data from production systems is only the beginning - those deletions must also reach all backups and replicas. Below, we explore how to implement retention policies and manage immutable archives in the context of distributed systems.
Setting Retention Policies for Backups
Retention policies aren't just for production systems; they must also cover all backup systems. When data is deleted from your primary system, you need a clear timeline for when that deletion will be reflected in your backups. For example, in a weekly backup cycle, deleted data could persist for up to seven days until the next backup overwrites it. This timeline should be documented in a retention matrix to avoid any ambiguity.
Legal holds can complicate things further. If certain logs need to be preserved due to litigation or investigations, those holds must apply consistently across all backups and replicas. Without proper coordination, some systems might delete critical evidence prematurely. Automating legal holds with TTL (Time-To-Live) settings and expiration tags ensures uniformity across all systems. These policies are critical for managing distributed systems and set the groundwork for addressing immutable archives.
Handling Immutable Archives and Replicated Data
Once retention policies are in place, managing immutable archives becomes the next challenge. These archives, often stored in WORM (Write Once, Read Many) systems, are essential for preserving forensic data but can conflict with GDPR's erasure requirements. To balance these needs, you must carefully document the retention duration of such archives and ensure they are isolated from active processes. Even if the data remains physically present, it should be inaccessible once archived.
For distributed systems that span multiple regions, a tiered storage strategy works best. Logs can move through three phases:
- Hot storage for real-time access
- Warm storage for periodic audits
- Cold storage (immutable archives) for long-term preservation
Each phase requires tailored access controls and retention timelines, as outlined below:
| Storage Phase | Retention Period | Access Level | Security Measures |
|---|---|---|---|
| Active Database | Up to 6 months | Operational teams | Real-time monitoring, Hot storage |
| Intermediate Archive | Defined by policy | Specific service teams | Hash verification, Warm storage |
| Final Archive | Until deletion | Restricted access | Immutable WORM storage, Cold storage |
Platforms like LogCentral simplify this process by automating the transition of logs across storage tiers and enforcing retention policies uniformly across distributed environments. With data hosted in France on EU-compliant infrastructure, LogCentral ensures that deletion rules are applied correctly. This approach reduces compliance risks while maintaining the forensic integrity necessary for regulatory audits.
Audit Controls and Compliance Monitoring
Once you've set up secure processes for managing log retention and disposal, the next step is implementing audit controls to ensure ongoing GDPR compliance. These controls aren't just a best practice - they're a legal requirement under GDPR. They also serve as evidence of compliance during regulatory reviews. Interestingly, statistics show that 9 out of 10 companies fail their first GDPR audit, with 65% of failures tied to poor data retention practices [4]. Additionally, about one-sixth of GDPR fines - averaging €4 million each - stem from excessive data retention [4].
Maintaining Retention Policy Documentation
Retention policy documentation is a key pillar of GDPR accountability. This includes creating and maintaining a retention schedule, a matrix, and a clear rationale for how long data is kept [4]. Records of Processing Activities (RoPA) are equally important, as they map out data flows and explain the purposes behind data processing [4].
"To be prepared in case of an audit by data protection authorities, businesses should ensure they securely maintain updated and accessible records of their data collection and processing."
– Tilman Harmeling, Senior Privacy Expert, Usercentrics [2]
It's not enough to just document policies - you also need proof that deletions are carried out as planned. This includes automated deletion logs, anonymisation workflows, access logs, and regular reviews of Role-Based Access Control (RBAC) permissions [4]. For permanent deletions, management approval should be documented, and external disposal services must provide destruction certificates. Assign staff to cross-check these certificates against the data sent for destruction [6]. A case in point: the French CNIL fined a remote clairvoyance service €250,000 for holding onto customer data up to six years after their business relationship ended. This demonstrates how seriously regulators take storage limits [2].
These measures collectively prepare businesses for compliance audits.
Conducting Regular Compliance Audits
Once your retention policies and documentation are in place, regular audits are crucial for spotting compliance gaps before regulators do. Quarterly reviews of retention policies help ensure they meet both regulatory requirements and evolving business needs. Additionally, periodically test your ability to retrieve and analyse archived or "cold" storage logs to confirm audit readiness [3].
To enhance accountability, maintain a "log of the logs" that tracks who accessed or modified log data and when [7]. For third-party vendors, include a "right to audit" clause in contracts and schedule annual reviews of their security practices [6]. This should involve assessing Data Processing Agreements (DPAs), reviewing storage infrastructure, and verifying deletion procedures [5]. Notably, many companies still retain data for an average of five years longer than necessary, either legally or operationally [4]. Regular audits can help address this common issue.
Vendor Management and Third-Party Compliance
When managing log data end-of-life risks, keeping an eye on third-party compliance is non-negotiable. Even if you rely on vendors for storing or disposing of logs, you’re still accountable for GDPR compliance - even if the vendor slips up. Article 28 of the GDPR makes it clear: you’re required to work only with processors who can provide "sufficient guarantees" that they have the right technical and organisational measures in place to meet GDPR standards [9]. This means you need to do more than just pick a vendor - you need to vet them thoroughly before signing contracts and keep tabs on their practices to ensure they align with your GDPR log management strategy.
Evaluating Third-Party Compliance
A solid contract is your first line of defense. Every processor or sub-processor handling your log data should agree in writing to delete or return all personal data once the agreement ends. The contract should spell out key details like the subject matter, duration, nature, and purpose of the processing, along with the types of personal data involved and the categories of data subjects [9].
You should also include audit rights in these agreements. This allows you to verify their compliance through periodic audits or even annual site visits to their storage facilities [8][9]. If they work with sub-processors, they must get your written approval beforehand and accept full responsibility for any failures on the part of those sub-processors [9]. These steps help ensure that everyone in the chain is meeting GDPR requirements.
Monitoring and Verifying Third-Party Practices
Once you’ve chosen a vendor, your job isn’t over. Regular checks are crucial to ensure they stick to GDPR rules. Conduct periodic spot-checks of their security processes, review their storage infrastructure and deletion methods annually, and request certificates of destruction for any log data they handle [6].
To avoid any risks of misuse or disclosure that could violate GDPR Articles 5(1)(f) and 32, keep a detailed log of all devices or physical records waiting to be destroyed - even if the vendor is handling them. Make sure contracts are signed off by senior management and explicitly include audit provisions [6].
Using LogCentral for GDPR-Compliant Log Management
If you're after a log management solution designed to meet GDPR requirements, LogCentral has been crafted specifically for European organisations. Developed in France to align with CNIL guidelines, it addresses the legal challenges often tied to international data transfers. This localised approach provides a solid foundation for managing GDPR-compliant logs with ease.
Key Features Supporting GDPR Compliance
LogCentral simplifies the management of log data through a three-phase lifecycle: Active (up to 6 months), Archive (secure and access-restricted), and Deletion (permanent and irreversible). When it comes to deletion, the platform uses secure wiping methods that comply with GDPR's "Right to Erasure" (Article 17). While personal data is permanently removed, metadata about the deletion - such as who performed it, when, and what was deleted - is retained for audit purposes, ensuring transparency without storing the actual data.
To help organisations reduce their data responsibilities, LogCentral includes data minimisation features. Real-time pseudonymisation and masking allow you to hash IP addresses, mask email details, and tokenise User IDs before the data even reaches storage. This reduces the amount of personal information under your management. For larger organisations and MSPs, the platform supports multi-tenancy to separate tenant data, while RBAC (Role-Based Access Control) and 2FA (Two-Factor Authentication) add layers of security. Compliance reports and alerts for upcoming deletion deadlines are also built in, making it easier to stay on top of GDPR retention rules. Plus, LogCentral offers straightforward pricing and a 7-day free trial - no credit card required.
Comparison with Alternative Solutions
LogCentral stands out for its compliance-first approach when compared to competitors like Graylog and OpenObserve. For example, while Graylog requires manual setup for custom retention policies and OpenObserve prioritises performance, LogCentral provides automated retention policies ranging from 6 to 12 months. Additionally, LogCentral performs client-side data masking in real time, whereas Graylog only supports post-processing masking, and OpenObserve offers fewer options altogether.
For French organisations, one of LogCentral's biggest advantages is its guarantee of EU data hosting within France, sidestepping the complexities of data sovereignty. By contrast, Graylog offers EU hosting as an optional feature, and OpenObserve requires self-hosting to achieve similar compliance. LogCentral also includes automated retention alerts and archive management as standard, eliminating the need for manual oversight often required by these competing platforms.
Wrapping Up
To stay compliant with GDPR and limit the potential impact of data breaches, it's crucial to align your log data retention and disposal practices with the regulation's requirements. By keeping only the data you truly need and ensuring it’s deleted promptly, you show accountability to both your customers and regulators like the CNIL.
The approach is simple: gather only the necessary information, clearly document retention periods along with their legal justifications, and use secure methods to dispose of data. Remember, GDPR's Article 17 mandates deletion within one month, so sticking to this timeline is non-negotiable.
In today’s fast-paced environments, managing logs manually just doesn’t cut it. Automation is the key to ensuring retention schedules are followed, handling complex multi-tenant setups, and maintaining reliable audit trails without risking human error. Tools like LogCentral make this process manageable, offering automated lifecycle management, client-side data masking, and EU-based hosting to address data sovereignty concerns effectively.
FAQs
Are IP addresses in logs personal data under GDPR in France?
Under GDPR in France, IP addresses are classified as personal data when they can identify individuals, whether directly or indirectly. This becomes particularly relevant when an IP address is paired with other information, like records from an Internet Service Provider (ISP). Ensuring the proper management and safeguarding of such data is crucial to remain compliant with GDPR requirements.
How do I handle GDPR deletions when logs also exist in backups?
When storing logs in backups, GDPR mandates clear retention policies. If a user requests their data to be erased, backups containing personal information must either be securely deleted or anonymized. This can get tricky, as removing data from backups often depends on the specific backup and recovery systems in place. To stay compliant, make sure your processes are thoroughly aligned with GDPR standards.
What documents do I need to prove log retention compliance to the CNIL?
To meet CNIL compliance standards, it's essential to keep a detailed record of processing activities. This includes documenting your policies for retaining and disposing of log data. These records should clearly specify the retention periods and the methods of disposal you use, ensuring everything aligns with GDPR regulations.