
EDR Playbooks for Automated Threat Response
EDR Playbooks for Automated Threat Response
EDR playbooks are automated workflows designed to handle security threats faster and more consistently. They help Security Operations Centers (SOCs) manage overwhelming alert volumes by automating repetitive tasks like isolating compromised devices, blocking malicious IPs, or disabling user accounts. This reduces response times from hours to seconds and minimizes human error.
Key Takeaways:
- What are they? Automated workflows triggered by specific security events or manual inputs.
- Why use them? To handle threats quickly, reduce manual effort, and ensure consistent responses.
- Core components: Triggers (event-based activations), conditions (filters for precision), and actions (tasks like containment or notifications).
- Examples: Automatically isolate a compromised endpoint or block a flagged IP at the firewall.
- Benefits: Reduced false positives, faster containment, and better focus for analysts on critical threats.
EDR playbooks integrate with tools like firewalls, identity providers, and threat intelligence platforms to deliver coordinated security responses. They’re essential for modern SOCs aiming to stay ahead of cyberattacks.
Microsoft Defender ATP-EDR Demo
Core Components of EDR Playbooks
EDR playbooks operate through three main components: triggers, conditions, and actions, enabling swift and dependable automated responses.
Triggering Conditions
Playbooks are activated when specific events occur within your security framework. Common triggers include the creation of a new incident, updates to existing incidents (like severity adjustments or status changes), or the generation of a security alert by an analytics rule [6]. For example, a playbook might automatically launch when a high-severity ransomware alert is detected by your EDR tool or when an analyst manually tags an incident with a specific label [5].
To ensure precise activation, triggers often employ property-based filters, activating only for alerts that meet specific criteria such as severity level, analytic rule names, or identifiers like IP addresses and hostnames [6]. More advanced setups utilize "custom details" - data extracted from raw event logs - to create nuanced triggers that only activate when multiple conditions are met simultaneously [6].
"A playbook does the work; runbooks guide human responses." - Swimlane [10]
In March 2023, Cisco introduced a triage playbook for a SOC integrated with Splunk Enterprise Security. This playbook automatically reviewed historical "notable events" from recent days. If a new alert matched a signature previously identified as a false positive, the playbook automatically closed the incident. This reduced the customer's event load from over 200 daily alerts to just 20, significantly cutting down the manual triage effort [7].
Next, we’ll explore how these triggers lead to automated responses.
Automated Actions and Workflows
Once initiated, playbooks execute predefined tasks to address threats. These tasks can range from straightforward actions, like creating a ServiceNow ticket or sending a Teams notification, to more decisive measures such as isolating a compromised device, blocking an IP address at the firewall, or disabling a user account in Microsoft Entra ID [8][4].
Modern playbooks use logical structures - such as if/then rules, loops, or switch cases - to streamline responses. For high-stakes actions, such as isolating a critical server or disabling an executive’s account, human oversight can be incorporated to ensure careful decision-making [1][3]. This balance allows organizations to combine the speed of automation with the prudence of human judgment.
Integration with Security Ecosystems
Effective playbooks don’t operate in isolation - they integrate seamlessly across your security ecosystem to deliver a coordinated response. Acting as the connective tissue between tools, they orchestrate actions across platforms [2][7]. This ensures that a single security event triggers coordinated measures across endpoints, firewalls, and identity providers [8][3].
"Automation is not about focusing on the individual tasks and steps; but it is about analysing processes and finding ways to reduce manual interventions." - Cisco Systems Inc [7]
The best integrations emphasize early enrichment. Instead of immediately jumping into containment, well-designed playbooks first gather critical context - evaluating asset importance, verifying IP reputation, or confirming user roles - before determining the appropriate course of action [9][10]. This approach minimizes false positives and avoids unnecessary disruptions. AI-driven triage systems can reduce false positives by up to 90%, allowing playbooks to focus on genuine threats [9].
Types of EDR Playbooks for Different Scenarios
Building on the components of playbooks, we can see how they adapt to address various security challenges. EDR playbooks are tailored to specific needs: triage playbooks validate alerts, containment playbooks stop threats in their tracks, and hunting playbooks seek out hidden dangers.
Incident Triage and False Positive Reduction
Triage playbooks are designed to validate alerts automatically. They do this by pulling insights from threat intelligence tools like VirusTotal and verifying user statuses through identity protection services like Microsoft Entra ID Protection. This process cuts down on false alarms significantly [4].
These playbooks also categorize threats, ensuring that critical incidents are prioritized for immediate attention. They suppress less urgent alerts, such as those triggered during routine maintenance, and correlate endpoint and network data to further reduce false positives [5][13][14].
By streamlining triage, these playbooks lay the groundwork for quick containment and proactive threat hunting.
Threat Containment and Remediation
Once a threat is confirmed, containment playbooks act fast to isolate compromised endpoints, stopping the spread of the attack [2][4]. For identity-based threats, they can disable compromised accounts, reset passwords, or revoke application permissions automatically [4][12]. On the network level, malicious IP addresses flagged in an alert can be blocked at the firewall [4].
Here’s a snapshot of common playbook actions for different scenarios:
| Scenario | Playbook Action | Integration Point |
|---|---|---|
| Compromised Machine | Isolate host from network | EDR (e.g., Defender for Endpoint) |
| Compromised User | Disable account / Reset password | Identity Provider (e.g., Entra ID) |
| Malicious Traffic | Block IP address | Firewall (e.g., Azure Firewall) |
After containment, remediation steps follow. These might include removing malicious files, terminating harmful processes, or restoring systems from backups to maintain business operations [14]. For high-stakes actions, playbooks often require manual approval through tools like Teams or Slack, where users can choose to "Block" or "Ignore" [4][14]. This approach ensures that containment measures are both effective and controlled.
Threat Hunting Playbooks
Unlike containment playbooks, hunting playbooks are proactive. They activate during investigations and focus on specific entities, updating IOC (Indicator of Compromise) watchlists and configuration databases automatically [2][4].
"Threat hunting begins where threat intelligence ends. It turns the insights of threat intelligence into concrete actions necessary to eradicate existing threats and prevent future attacks." – IBM [15]
These playbooks analyze logs from multiple sources, uncovering threats that evade traditional defenses [11][13]. For example, in 2024, eSentire's Threat Response Unit conducted over 162,300 indicator-based threat sweeps and more than 1,190 hypothesis-driven threat hunts [17]. Insights from these hunts feed back into containment playbooks and detection rules, creating a cycle of continuous improvement that bolsters the entire response system [16][17].
Best Practices for Building EDR Playbooks
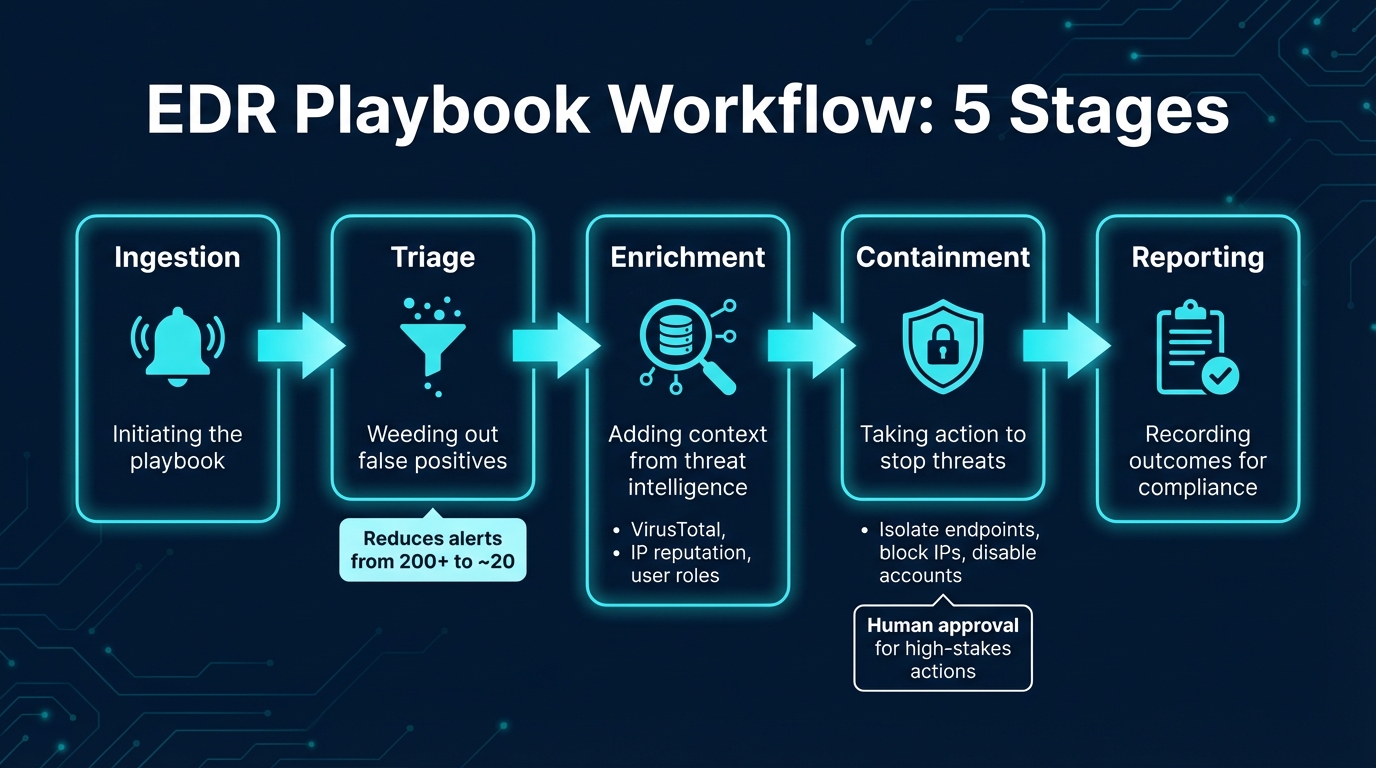
EDR Playbook Workflow: 5 Stages from Ingestion to Reporting
Creating effective EDR (Endpoint Detection and Response) playbooks requires careful planning, seamless integration, and ongoing adjustments. Once the foundational elements are in place, the next step is crafting logical workflows that enable smooth automation.
Designing Logical Workflows
A well-designed workflow typically follows these stages: Ingestion (initiating the playbook), Triage (weeding out false positives), Enrichment (adding context), Containment (taking action), and Reporting (recording outcomes) [7]. To simplify complex playbooks, break them into smaller, reusable modules. For instance, an "IP Enrichment" module can be shared across multiple playbooks, saving time and effort.
Start by sketching your workflow or drafting pseudocode. This helps you identify key decision points - like distinguishing between internal and external IPs - and plan for potential errors, such as a missing incident ID. In one example, a triage playbook reduced event volume from over 200 to roughly 20 by implementing filters at each step [7].
For actions with significant impact, include steps requiring human approval, like adaptive cards in Teams or Slack. This balances automation with oversight. Also, verify all inputs at the beginning of the workflow to prevent failures mid-process [1], and stick to consistent naming conventions for variables to make the playbook easier to maintain [7].
Using Threat Intelligence
Incorporating threat intelligence elevates playbooks from simple automation tools to dynamic defense systems. By querying external sources like VirusTotal for IPs, URLs, or file hashes, playbooks can enrich incidents with valuable context [4]. During the triage phase, this enrichment helps distinguish false positives by comparing event signatures with historical data and known malicious indicators [7].
For containment, playbooks can act on specific Indicators of Compromise (IOCs), such as malicious file hashes or domains, to trigger actions like blocking or isolating threats. Real-time threat intelligence feeds add another layer of adaptability, enabling playbooks to respond to emerging threats without manual updates [4]. Focus on triage and enrichment phases before automating containment, and use entity triggers to pull reputation reports for suspicious files during threat-hunting activities [4].
Testing and Optimising Playbooks
Even a well-crafted playbook needs rigorous testing before going live. Start by deploying it in detect-only mode on a limited set of endpoints, and validate its performance in a sandbox environment that mirrors your production setup, including matching OS versions, applications, and security tools [18][19][20]. Use version control and automated testing to ensure reliability [21].
SOC teams often face thousands of alerts daily, many of which are false positives [19]. To keep playbooks effective, schedule regular tuning sessions to review alert patterns and adjust thresholds based on what’s considered normal behavior [18][21]. Additionally, map playbook actions and detection rules to the MITRE ATT&CK framework to identify any gaps in visibility and ensure comprehensive coverage of the attack lifecycle [19][21].
"Detection engineering is a continuous lifecycle of developing, validating, and fine-tuning security alerts so that defenders can more easily spot true threats with fewer false alarms" - SimSpace [19]
This cycle of testing and fine-tuning helps maintain the effectiveness of your playbooks as the threat landscape evolves.
How LogCentral Supports EDR Playbooks
EDR playbooks rely heavily on consistent syslog data and network telemetry to function effectively. LogCentral delivers this foundation by offering centralised syslog management, which feeds security events directly into automated workflows. Fully hosted in Europe and adhering to GDPR standards, it’s an ideal solution for businesses and MSPs navigating the EU's regulatory landscape. Here’s how LogCentral strengthens automated threat response across various environments.
Native Multi-Tenancy and Real-Time Monitoring
For MSPs managing multiple clients, LogCentral's native multi-tenancy feature enables security teams to monitor active playbooks across all environments from a single dashboard. This unified view allows teams to track security events and initiate automated responses across different tenants simultaneously. Coupled with 24/7 monitoring, the platform ensures continuous event capture, providing the real-time data streams necessary for EDR playbooks to identify and respond to threats as they arise.
Through centralised permissions, MSPs can also trigger containment actions in customer environments without manual steps - critical when response times are measured in seconds rather than hours.
Integration with Cisco Meraki and Other Platforms
LogCentral goes beyond centralised management by offering seamless integrations to enhance automated responses. Its native Cisco Meraki integration enables playbooks to block network threats instantly. For example, when a playbook flags a malicious IP address, URL, or domain using threat intelligence, it can trigger automatic blocking at the Meraki MX perimeter. This integration provides essential sightings data, helping playbooks differentiate between legitimate traffic and actual threats [24].
Additionally, LogCentral’s ability to process network telemetry from various sources ensures no blind spots in complex environments. This comprehensive visibility feeds into incident correlation, giving playbooks the full context needed to make precise decisions across the security ecosystem.
Alert Management and Automation
LogCentral’s intelligent alerting system serves as a key trigger for EDR playbooks. By filtering out noise and prioritising critical threats, it ensures playbooks activate only for genuine incidents. Actions are automatically documented to support GDPR compliance [6][5][23]. This noise reduction is crucial for SOC teams, who often face thousands of alerts daily, many of which could otherwise lead to unnecessary playbook activations.
"With such a small window of response time, you need to have not just good detection but automated responses that you build very easily..." - Dave Coughanour, VP of Cybersecurity at ANSYS [22]
LogCentral achieves this through its architecture, which is designed to integrate seamlessly with other platforms, streamlining the automation of threat detection and response.
Conclusion
EDR playbooks transform cybersecurity from a constant scramble to a more controlled and automated defense strategy. By streamlining response procedures and enabling containment actions at machine speed, organisations can slash their Mean Time to Respond (MTTR) by as much as 10 times[22]. Success depends on combining smart triggering conditions, well-thought-out workflows, and smooth integration within your existing security tools.
One of the biggest hurdles for modern SOC teams is alert fatigue, and automated playbooks offer a practical solution. When configured effectively, they can group related alerts, reducing investigation volumes by up to 98%[25]. This means analysts can concentrate on real threats instead of drowning in false positives. Additionally, automated enrichment from threat intelligence sources provides the crucial context analysts need to make informed decisions.
Speed matters in cybersecurity, as industry benchmarks clearly show[22]. For European organisations juggling multiple environments, LogCentral's GDPR-compliant, multi-tenant platform with native Cisco Meraki integration ensures automated and compliant threat response, tailored to their unique needs.
FAQs
How can EDR playbooks help SOCs respond to threats more quickly?
EDR playbooks are a game-changer for Security Operations Centers (SOCs), simplifying threat detection and response by automating repetitive tasks. This automation significantly cuts down the time it takes to identify, contain, and address security threats, freeing up teams to tackle more intricate challenges.
By setting predefined actions for routine issues - like isolating a compromised device or blocking a malicious IP address - playbooks help ensure responses are both faster and more consistent. They also lower the risk of human error, which is especially valuable during high-stress incidents, helping SOC teams maintain peak efficiency.
For businesses in France, tools like LogCentral add an extra layer of support. With advanced log management, smart alerts, and smooth integrations, these tools make handling and responding to security incidents far more manageable and effective.
What are the key components of a successful EDR playbook?
A solid EDR (Endpoint Detection and Response) playbook is built around a few key elements that ensure threats are managed efficiently and with minimal manual intervention. These elements typically include well-defined response procedures, automation workflows, and decision points that guide actions based on the specific threat scenario. For instance, a playbook should clearly outline the steps for containment, investigation, and remediation of incidents, ensuring that responses are both structured and consistent.
Another critical aspect is detailing roles and responsibilities within the team. This ensures everyone knows their part in the process. Additionally, automating repetitive tasks through scripts or integrations can significantly reduce manual effort and the risk of human error. Decision points within the playbook should remain adaptable, allowing teams to escalate or modify actions depending on the threat’s severity. To make responses more streamlined, using templates for common issues like malware infections or phishing attempts can help IT teams act faster and more effectively.
For businesses in France, platforms like LogCentral offer tools that can elevate EDR playbook execution. With features such as intelligent alerts, real-time log visualisation, and automated firewall management, these solutions simplify both threat detection and response. Moreover, they ensure compliance with GDPR regulations, which is essential for organisations operating within Europe.
How does LogCentral improve EDR playbooks for automated threat response?
LogCentral strengthens EDR playbooks by offering a powerful log management solution that fits smoothly into automated threat detection and response workflows. Thanks to its real-time log monitoring and analysis, IT teams can swiftly pinpoint security issues and activate playbook actions based on specific patterns. Features like smart alerts and long-term log storage ensure constant oversight and compliance, boosting the reliability and efficiency of automated responses.
With built-in integrations, such as Cisco Meraki, LogCentral enhances playbooks by adding contextual data that enables precise automated actions, like firewall adjustments or IP management, cutting down on the need for manual input. Tailored for GDPR compliance and EU-based hosting, LogCentral is an excellent fit for organisations in France and across Europe, ensuring adherence to regulations while supporting scalable and efficient threat response operations.