
Configure syslog server settings in Watchguard Fireware
Configure syslog server settings in Watchguard Fireware
Want to centralize your network logs for better security and troubleshooting? Configuring syslog servers in Watchguard Fireware can help. Here's what you need to know:
- Supported Versions: Fireware v12.4+ supports sending logs to up to 3 syslog servers.
- Key Benefits:
- Centralized log storage.
- Real-time security monitoring.
- Simplified compliance and troubleshooting.
- Setup Checklist:
- Ensure your syslog server is ready (port 514 open, static IP, trusted network).
- Verify compatibility with standard Syslog or IBM LEEF formats.
- Configuration Steps:
- Log in to Fireware Web UI or Policy Manager.
- Enable syslog and add server details (IP address, port, log format).
- Assign log types (e.g., alarms, traffic, events) to syslog facilities.
For advanced monitoring and compliance, integrate logs with LogCentral, which offers dashboards, alerts, and long-term storage. Follow these steps to enhance your network security and streamline log management.
Setup Requirements
Make sure to complete these steps before configuring syslog settings in Watchguard Fireware.
Compatible Fireware Versions
To use the multi-server feature, you'll need Watchguard Fireware v12.4 or later. This version allows you to send log messages to multiple syslog servers at the same time. After ensuring your Fireware version is up to date, set up your syslog server to handle log transmission.
Server Setup Needs
Your syslog (or QRadar) server must be ready and functioning before connecting it to your Firebox. Here's what you need:
-
Basic Server Configuration
- Install syslog server software correctly.
- Set up log reception settings.
-
Log Format Compatibility
- Ensure support for standard Syslog format.
- Verify compatibility with IBM LEEF (Log Event Extended Format).
-
Security Considerations
Since syslog messages are sent without encryption, place your server on a trusted network to maintain security [1].
These configurations help integrate with platforms like LogCentral for centralized logging.
Network Setup Checklist
Proper network configuration is key to consistent log transmission. Check the following:
| Setting | Requirement | Notes |
|---|---|---|
| Default Port | 514 | Standard syslog port |
| Network Placement | Trusted Network | Enhances security |
| IP Configuration | Static IP | Ensures stable connectivity |
| Firewall Rules | Allow TCP/UDP 514 | Both protocols may be needed |
Review and test all these components thoroughly to ensure smooth and secure logging before finalizing your setup.
Configuration Steps
Once you've completed the prerequisites, follow these steps to configure your syslog settings.
Opening Syslog Settings
To access syslog settings through the Fireware Web UI:
- Log in to your Fireware Web UI.
- Go to System > Logging.
- Select the Syslog Server tab.
If you're using Policy Manager, open these settings by navigating to Setup > Logging in the main menu.
Now, you're ready to set up the syslog output parameters.
Setting Up Syslog Output
Follow these steps to configure syslog output:
1. Enable Syslog Transmission
Select the option "Send log messages to these syslog servers" to enable syslog. Fireware version 12.4 and later allows sending logs to up to three servers.
2. Configure Server Details
Click "Add" and provide the following details:
- IP Address: Enter the IP address of your syslog server.
- Port: Default is 514, the standard port for syslog.
- Log Format: Choose either Syslog or IBM LEEF.
3. Additional Settings
Enable these options as needed:
- Include a time stamp (available for Syslog format only).
- Add the device serial number.
- Include a syslog header (available for IBM LEEF format only).
Choosing Log Types
Assign syslog facilities to organize logs by type. Here's a quick reference:
| Log Type | Recommended Facility | Priority Level | Notes |
|---|---|---|---|
| Alarm | Local0 | Highest | Critical security alerts |
| Traffic | Local1 | High | Network traffic data |
| Event | Local2 | Medium | System events |
| Diagnostic | Local3 | Low | Troubleshooting information |
| Performance | Local4 | Lowest | System metrics |
Note: If you're using the IBM LEEF format, only messages with the msg-id field will be sent. Performance logs are excluded by default in this format.
Testing Your Setup
After setting up your syslog configuration, it’s important to confirm that everything is working as expected. Here's how to validate connectivity and ensure log accuracy.
Connection Test Steps
-
Network Connectivity Test
Use the Firebox CLI to ping the syslog server and confirm basic connectivity:ping [syslog-server-ip] -
Port Verification
Make sure port 514 is open. You can do this by setting up a firewall policy with logging enabled and then testing the connection. -
Log Generation Test
Turn on diagnostic logging temporarily, apply some configuration changes, and check if the syslog server receives the test messages.
Log Verification
For Syslog Format:
- Confirm timestamps align with the configured timezone.
- Check for the Firebox serial number if that option is enabled.
- Ensure messages are assigned the correct facilities.
For IBM LEEF Format:
- Confirm the LEEF header is properly structured.
- Verify the presence of the
msg-idfield. - Ensure the vendor name is listed as "WatchGuard."
- Check that the product version matches the Fireware version.
If logs don’t look right or seem incomplete, refer to the common issues and fixes below.
Common Problems and Fixes
| Problem | Likely Cause | Solution |
|---|---|---|
| No logs received | Network connectivity | Check firewall rules and routing. |
| Incomplete logs | Facility misconfiguration | Review and adjust facility settings. |
| Timestamp issues | Time synchronization | Enable NTP on both devices. |
| Format errors | LEEF/Syslog mismatch | Confirm server format compatibility. |
Important: Syslog messages are not encrypted, so it’s crucial to keep your syslog server on a trusted network segment [1].
Once logs are verified, you can import them into LogCentral for streamlined monitoring and analysis.
LogCentral vs Other Solutions
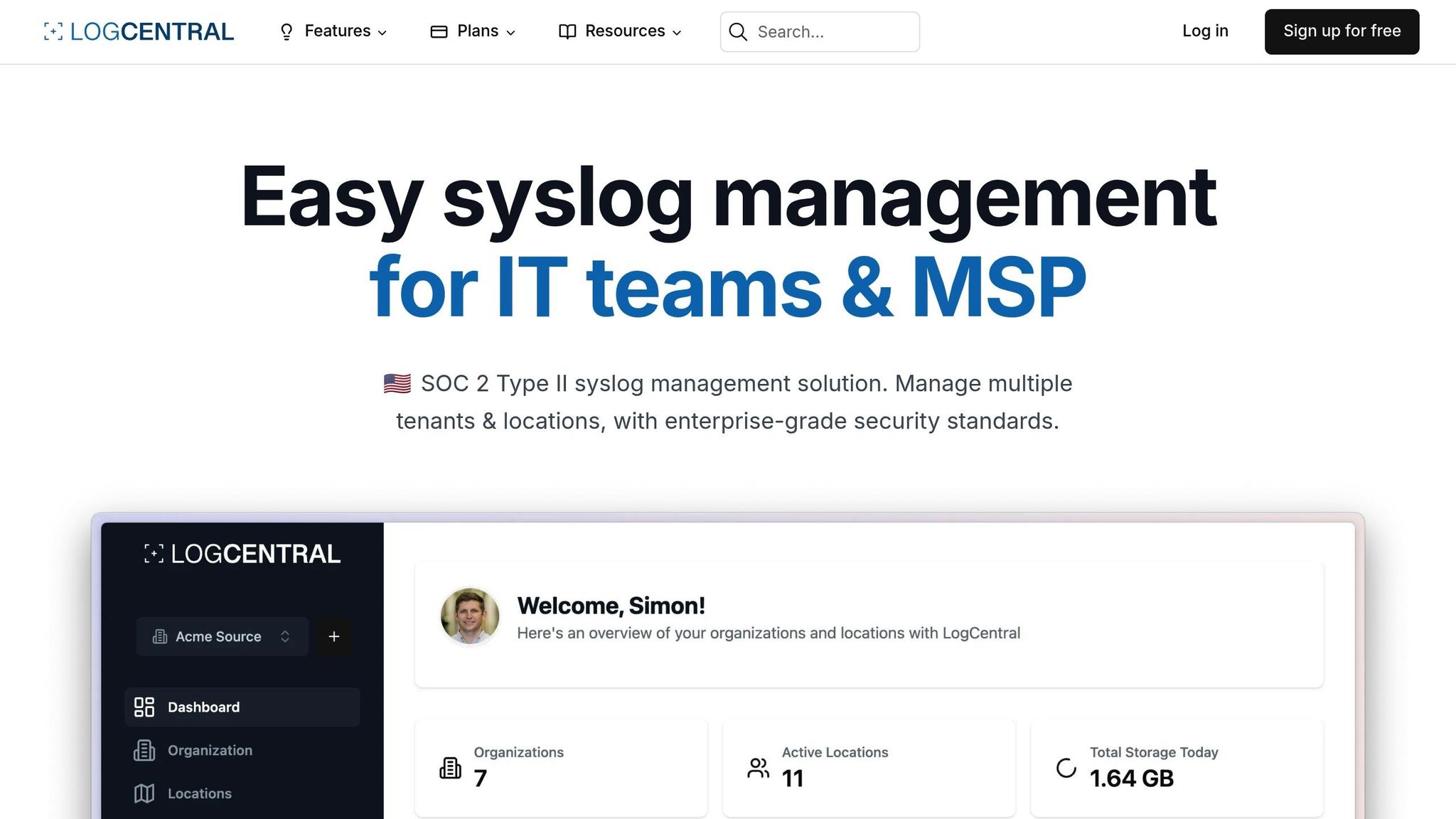
Once syslog configuration and testing are complete, choosing the right management platform is key to effective analysis. LogCentral brings features specifically tailored for Watchguard environments, making it a strong contender.
LogCentral Main Features
LogCentral offers tools designed to simplify and enhance syslog management for Watchguard Fireware users:
- Multi-tenancy Support: Makes it easier to manage multiple Watchguard devices across clients or departments.
- Advanced Visualization: Provides custom dashboards to monitor security events.
- Compliance Tools: Automates regulatory tasks, reducing manual effort.
- Intelligent Alerting: Cuts down on false positives and highlights critical events.
- Extended Storage: Offers flexible options for keeping historical logs.
These features give LogCentral an edge, as seen in the comparison below.
Platform Comparison Table
| Feature | LogCentral | Traditional Syslog Servers | Enterprise SIEM Solutions |
|---|---|---|---|
| Multi-tenancy | Built-in support | Manual separation required | Available but complex to set up |
| GDPR Compliance | Automated tools | Requires manual setup | Needs extensive configuration |
| Log Visualization | Real-time dashboards | Basic text-based logging | Advanced but hard to configure |
| Alert Management | Smart filtering | Basic alerts only | Comprehensive but complex |
| User Management | Built-in RBAC (role-based access control) | Limited options | Full features, but complex setup |
| Pricing Model | Tiered with free trial | Self-hosted costs | Expensive enterprise licensing |
Traditional syslog servers provide basic functionality but demand significant upkeep. Enterprise SIEM solutions, while feature-rich, often involve complicated setups. LogCentral bridges the gap by offering advanced tools with a simpler implementation process. This allows teams to focus on gaining security insights rather than dealing with infrastructure headaches.
Summary
Setup Steps Review
Follow these steps to configure WatchGuard Fireware's syslog settings:
- Pre-run Check: Make sure your syslog server is up and running.
- Access Settings: Open the syslog settings through the Web UI (System > Logging) or Policy Manager (Setup > Logging).
- Add Servers: Enter the IP addresses and ports for up to three syslog servers (available on Fireware v12.4+).
- Choose Format: Pick either the standard Syslog format or IBM LEEF format.
- Set Options: Adjust settings like timestamp, serial number, and facility levels.
For high-priority messages (like alarms), assign them to the Local0 facility. These steps prepare your logs for better analysis with LogCentral.
LogCentral Benefits
Once syslog settings are configured, LogCentral enhances your monitoring with features like:
- Support for managing multiple WatchGuard Fireboxes
- Round-the-clock monitoring paired with smart alerts
- Tools to assist with GDPR compliance
- Real-time visualization dashboards
- Long-term log storage
- Role-based access control (RBAC) for secure management