
Zero Trust Logging: Why “Verify Everything” Means Logging Everything
Zero Trust Logging: Why “Verify Everything” Means Logging Everything
Zero Trust security means you verify every access request - and that requires logging everything. Logs provide the data needed to detect threats, analyze incidents, and maintain security. Here’s why logging is essential and how it supports Zero Trust:
- Continuous Verification: Logs track user actions, system changes, and network activity to identify unusual behavior.
- Policy Engine Support: Detailed logs feed Zero Trust decision-making systems for precise access control.
- Deep Observability: Advanced logging techniques, like network behavior analysis, help uncover hidden threats.
Key Log Types for Zero Trust:
- User Access Logs: Monitor login attempts, permission changes, and session activity.
- System & Network Logs: Track traffic patterns, system events, and security alerts.
- Device Security Logs: Ensure endpoints comply with security policies and detect tampering.
Quick Setup Tips:
- Use a central log management system to collect and analyze logs.
- Improve log quality with consistent formats, contextual data, and validation.
- Automate analysis to prioritize critical events and reduce manual work.
Efficient logging is the backbone of Zero Trust. Without it, you can’t verify or secure your systems effectively.
Required Log Types for Zero Trust
To successfully implement a Zero Trust security model, comprehensive logging across various domains is essential. Below, we’ll dive into the key log types that form the backbone of a Zero Trust framework.
User Access and Login Logs
User access logs capture details about who is accessing your systems, making them a cornerstone of Zero Trust monitoring. These logs help track login events, changes in permissions, and user session activity.
Here’s what to focus on:
- Authentication Events: Record both successful and failed login attempts to identify unusual patterns or potential threats.
- Permission Changes: Log updates to user access rights to ensure proper oversight of privileges.
- Session Data: Monitor the duration and activity of user sessions for any irregularities.
"A log is a record of the events occurring within an organization's systems and networks... Logs have evolved to contain information related to many different types of events occurring within networks and systems. Within an organization, many logs contain records related to computer security; common examples of these computer security logs are audit logs that track user authentication attempts and security device logs that record possible attacks." - NIST SP 800-92
System and Network Logs
System and network logs provide critical insights into security and operational health. They help establish a baseline for normal behavior, making it easier to spot anomalies that could indicate a threat.
| Log Type | Purpose | Key Metrics |
|---|---|---|
| Network Traffic | Monitor data flow patterns | Source/destination IPs, protocols, packet sizes |
| System Events | Track system-level changes | Configuration updates, service starts/stops |
| Security Alerts | Detect and respond to threats | Intrusion attempts, malware indicators |
"Agency maintains visibility into communication across all agency networks and environments while enabling enterprise-wide situational awareness and advanced monitoring capabilities that automate telemetry correlation across all detection sources." - CISA, Zero Trust Maturity Model v2.0
Device Security Logs
Device security logs ensure that endpoints comply with security policies, verifying that only trusted devices interact with sensitive resources. These logs are indispensable for maintaining device-level security in a Zero Trust environment.
Key elements to track include:
- Security Status: Monitor current patch levels and security configurations to identify vulnerabilities.
- Compliance Checks: Verify adherence to organizational security policies.
- Hardware Changes: Detect new peripheral connections or hardware modifications that could signal tampering.
- Software Installation: Keep an eye on application installations and updates to prevent unauthorized software from being introduced.
According to the MITRE ATT&CK framework, Defense Evasion accounts for 43 documented attack techniques, making it the largest category of attack methods. This highlights the need for thorough device logging to detect and counter evasion tactics.
Together, these log types lay the groundwork for effective Zero Trust monitoring, setting the stage for the detailed implementation guide to follow.
Zero Trust Logging Setup Guide for SMBs
Setting Up Central Log Management
For small and medium-sized businesses, centralizing log management is a critical first step in implementing a Zero Trust approach.
A well-structured central log management setup should include:
- Log Collection Points: Configure network devices, servers, and applications to forward logs to a central system. Tools like LogCentral offer features such as multi-tenancy to keep logs from different sources separate while ensuring GDPR compliance.
- Data Retention Settings: Define retention periods based on compliance requirements. LogCentral's long-term retention options can help optimize storage costs.
- Access Controls: Apply role-based access control (RBAC) to ensure only authorized personnel can view or manage logs.
These foundational steps create a solid framework for effective telemetry, laying the groundwork for high-quality log data.
Improving Log Data Quality
Good telemetry starts with good data. As Ian Farquhar aptly puts it, "garbage in, garbage out is still a thing" [1].
| Data Quality Aspect | Approach | Expected Outcome |
|---|---|---|
| Standardisation | Use consistent timestamp formats and log structures | Easier correlation and analysis |
| Contextual Data | Add user IDs, device details, and location info | More effective incident investigations |
| Data Validation | Check log integrity and completeness | Increased reliability of log data |
Once the data quality is assured, you can move on to fully integrating Zero Trust logging into your operations.
Step-by-Step Zero Trust Logging
-
Initial Setup
Configure your central log system to capture critical events, such as:- Authentication attempts
- Network traffic details
- System configuration changes
- Security alerts
-
Enhanced Monitoring
Deploy tools and techniques for deeper observability to gain a comprehensive understanding of your environment. -
Integration and Correlation
Combine data from various sources, including operating systems, applications, security agents, network behaviors, and hypervisors, to create a unified security view. -
Automation and Analysis
Automate the analysis process to make logs actionable:- Set up real-time alerts
- Define behavioral baselines
- Correlate events automatically
- Leverage AI and machine learning to identify patterns and anomalies
Zero Trust logging is about more than just collecting data - it's about turning that data into actionable insights. As the Cybersecurity and Infrastructure Security Agency (CISA) explains, "CISA applies the term visibility to refer to (a) the observable artifacts of digital events and (b) the characteristics of the digital environment in which those events take place" [1].
Common Zero Trust Logging Problems
Reducing Log Overload
Handling an overwhelming amount of log data can be tricky, but there are ways to stay on top of it:
- Use Smart Filtering: Set up rules to capture the most important security events, such as login attempts, privilege escalations, and configuration changes. This helps cut out the everyday noise.
- Prioritize Events by Severity: Assign severity levels to events in your logs. For instance, focus on high-priority incidents like failed logins or unauthorized privilege changes before diving into less urgent routine activities.
- Automate Log Analysis: Leverage automated tools to spot patterns and anomalies in your logs. This reduces the need for manual reviews and speeds up your response to potential threats.
These strategies not only make log management more efficient but also help keep resources in check while maintaining visibility.
Managing Log Storage Costs
Finding the right balance between collecting comprehensive logs and managing storage expenses is crucial:
- Use Tiered Log Rotation and Retention: Develop a system where critical logs are kept for longer periods, while less sensitive data is cycled out sooner.
- Focus on Actionable Data: As CISA explains, "CISA applies the term visibility to refer to (a) the observable artifacts of digital events and (b) the characteristics of the digital environment in which those events take place" [1]. Concentrate on retaining logs that directly impact your security measures, and regularly review your retention policies to ensure they align with both your security needs and storage budget.
LogCentral for Zero Trust Implementation
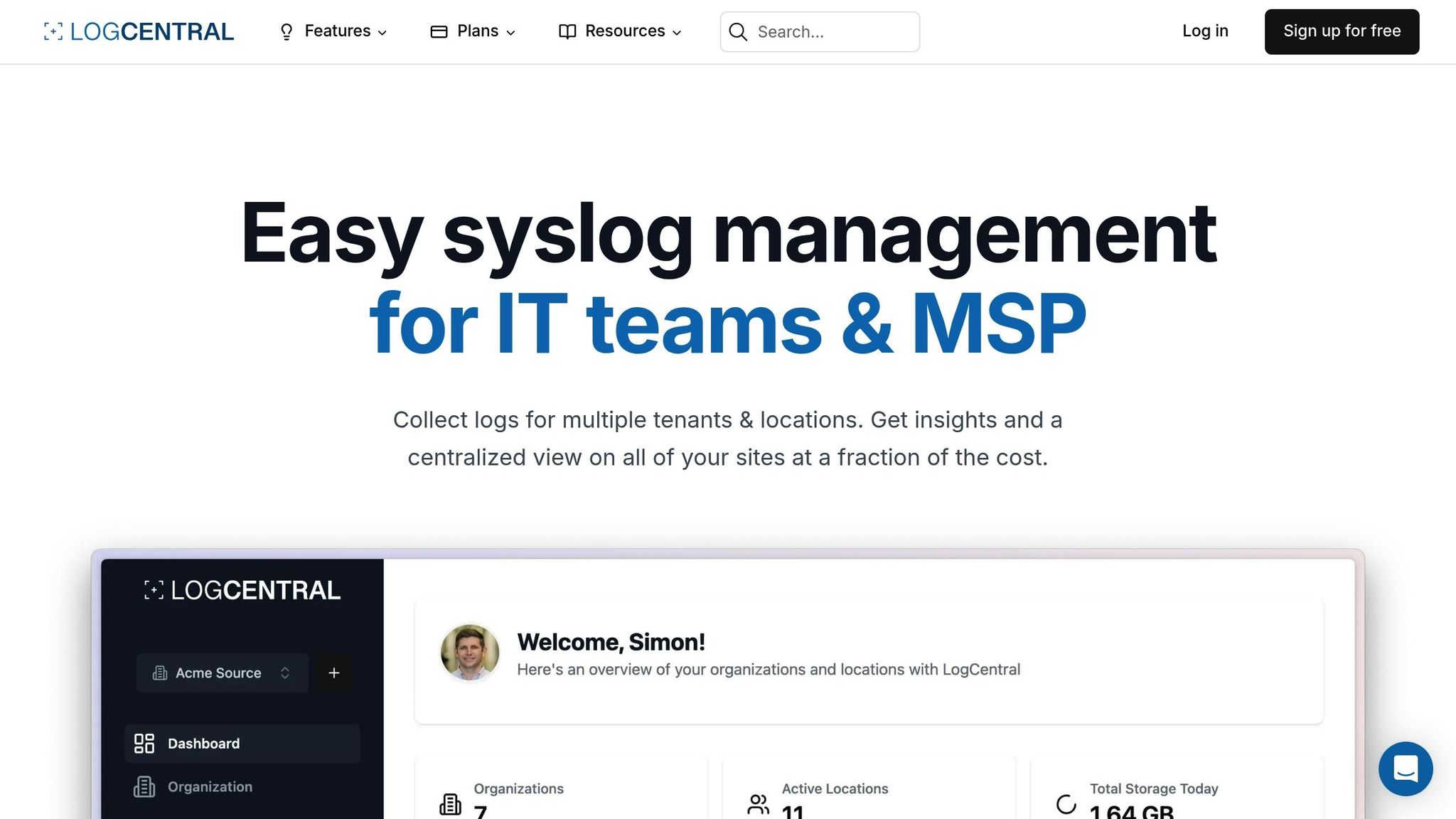
As mentioned earlier, thorough logging is a cornerstone of Zero Trust security, and LogCentral is designed to meet these needs head-on with its robust features.
Zero Trust Security Features
LogCentral aligns perfectly with Zero Trust principles by offering continuous monitoring, live visualization, and intelligent alerts - all while adhering to GDPR standards and operating from a Europe-based platform.
Here’s a closer look at its key features:
- 24/7 Monitoring: Constant oversight to detect and address threats in real-time.
- Live Log Visualization: Immediate access to log data for quick analysis.
- Intelligent Alerts: Notifications powered by smart algorithms to prioritize critical issues.
Other helpful tools include Long-term Retention for historical data, Smart IP Management for efficient network control, and Role-Based Access Control (RBAC) to ensure secure access.
Platform Comparison
LogCentral doesn’t just log events - it simplifies Zero Trust security with advanced features like automatic firewalling, a multi-client-friendly infrastructure, and centralized management. Here's how it stacks up against competitors:
| Feature | LogCentral | Competitor Platforms | Zero Trust Advantage |
|---|---|---|---|
| Data Location | Europe-based hosting | Varies | GDPR compliance |
| Multi-tenancy | Native support | Often requires add-ons | Better isolation |
| Integration | Cisco Meraki native support | Limited vendor compatibility | Improved visibility |
| Access Control | Built-in RBAC | Basic user management | Enhanced verification |
These features make LogCentral a powerful tool for implementing Zero Trust strategies, offering both security and operational efficiency. Its capabilities set the foundation for exploring practical steps to deploy Zero Trust effectively.
Conclusion: Building Zero Trust with Logging
Logging forms the backbone of a Zero Trust security strategy. Reliable telemetry serves as the cornerstone for implementing effective controls across an organisation, ensuring a robust security posture.
Effective logging captures a wide range of data, including user authentications, system modifications, and network activity patterns. This aligns with established security practices that highlight the importance of log data for maintaining visibility and control in a secure environment.
Three core aspects define successful logging in a Zero Trust framework:
- Comprehensive Visibility: Gathering observable data points across your entire digital ecosystem.
- Continuous Analysis: Monitoring in real time to distinguish between normal and suspicious activities.
- Correlated Telemetry: Integrating data from multiple sources to improve threat detection capabilities.
LogCentral, as previously discussed, brings these principles to life with its integrated logging platform. Designed to meet rigorous EU data protection standards, LogCentral offers advanced features like continuous monitoring, live data visualisation, and intelligent alerting - all essential for Zero Trust security.
The detailed documentation from the MITRE ATT&CK framework highlights the importance of strong logging practices in defending against evasion techniques [1]. By leveraging LogCentral’s capabilities, organisations can establish a secure foundation for their Zero Trust model while adhering to European data protection regulations.
This approach not only enhances security visibility but also enables informed decision-making, paving the way for a successful Zero Trust implementation across your infrastructure.
FAQs
How does Zero Trust logging enhance an organisation's ability to detect and respond to threats?
The Role of Logging in Zero Trust Architecture
In a Zero Trust framework, logging is indispensable for spotting and addressing potential threats. By gathering detailed telemetry - like user activities, login attempts, changes in privileges, and system updates - you create a foundation for continuously assessing access requests and identifying unusual behavior as it happens.
This steady stream of data directly powers policy engines, ensuring decisions are always grounded in the most current and relevant information. Without strong logging practices, verifying activity or enforcing security protocols becomes a guessing game. By tracking everything - from unsuccessful login attempts to data access events - organisations gain the clarity they need to respond swiftly and effectively to security risks.
What should you consider when setting up a centralised log management system for Zero Trust?
To create a strong centralised log management system for a Zero Trust strategy, start by focusing on detailed logging and reliable telemetry. Capture all critical events, including login attempts (both successful and failed), privilege modifications, and data access activities. These logs serve as the backbone for assessing and enforcing access policies.
Make sure your log data is well-structured, time-synchronised, and rich in context to support precise decision-making. Regular log reviews and analysis are key to spotting risks and refining your system's performance. By emphasising consistent and high-quality logs, you’ll improve policy enforcement and fortify your Zero Trust approach.
How can SMBs control log storage costs while ensuring effective Zero Trust logging?
Managing log storage costs while sticking to Zero Trust principles doesn't have to be a headache. A well-thought-out plan can make all the difference. Start by prioritizing critical logs - focus on capturing high-value data like authentication attempts, privilege changes, and access to sensitive information. This way, your Zero Trust policy engine gets the data it needs without overloading your storage.
You can also implement log retention policies to keep things under control. For instance, archive older logs or delete less essential data after a specific period, as long as it aligns with regulations like GDPR. On top of that, techniques like log compression and deduplication can help shrink storage needs while preserving data accuracy.
For added flexibility, look into scalable cloud-based storage options. These solutions, such as LogCentral, let you pay for just the storage you use. This approach is especially handy for SMBs, balancing cost-effectiveness with comprehensive logging to support a strong Zero Trust framework.